This document summarizes all new features and bug fixes for version 5.14 as well as breaking changes when being upgraded from previous versions.
New features and improvements
IdentifyMe application
We have added many more useful features to the IdentifyMe application:
Reset password without entering current password
IdentifyMe supports resetting passwords without entering current passwords. This feature is useful when you can authenticate your users using an Identity Provider that has a high level of assurance such as NemID or MitID.
To learn more about this feature, please visit IdentifyMe - password management
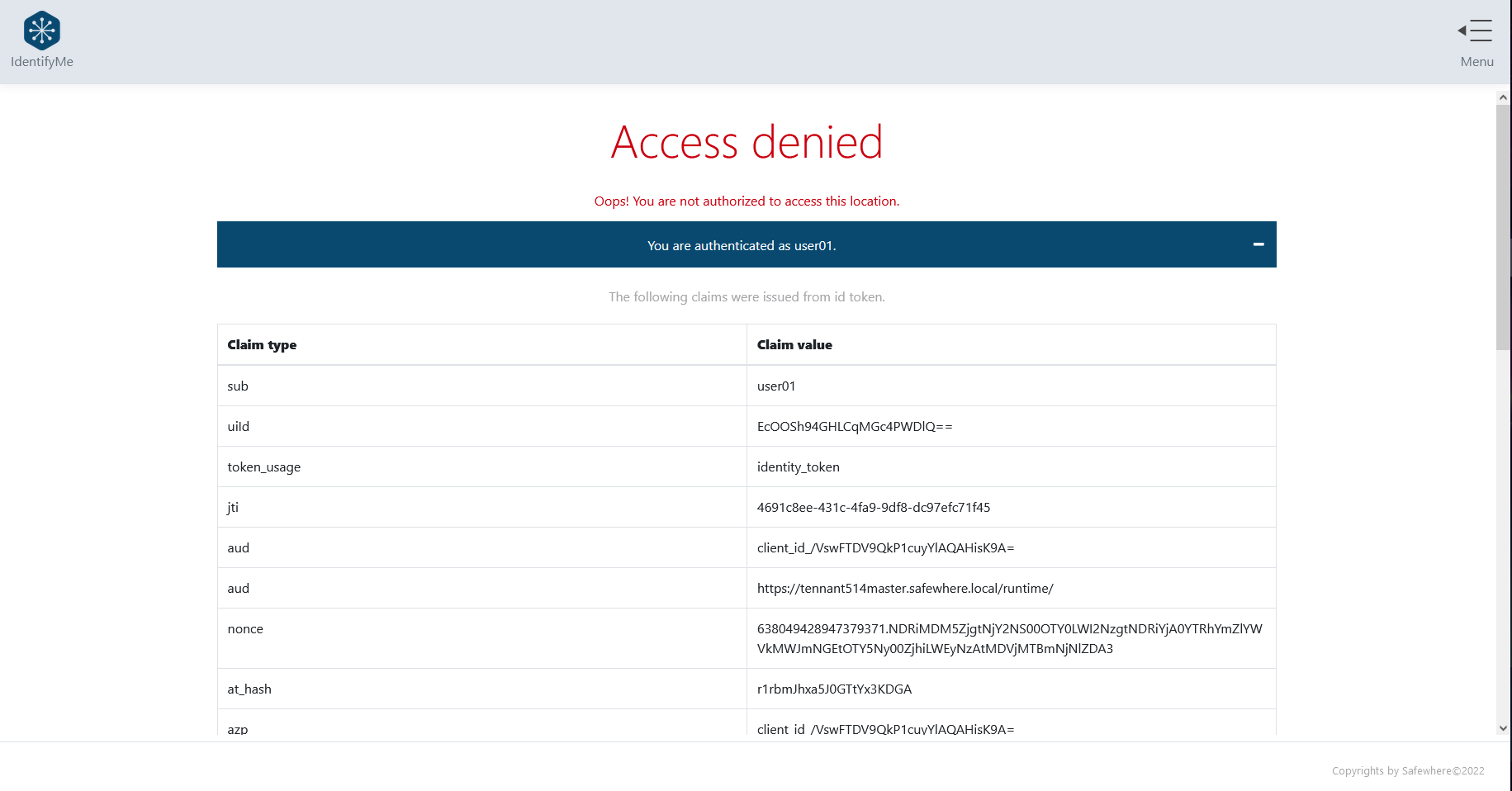
Display the Access Denied page when the user's token does not have necessary claims
IdentifyMe shows the Access denied page when:
-
The user's token does not have the urn:identify:rest-api:role claim
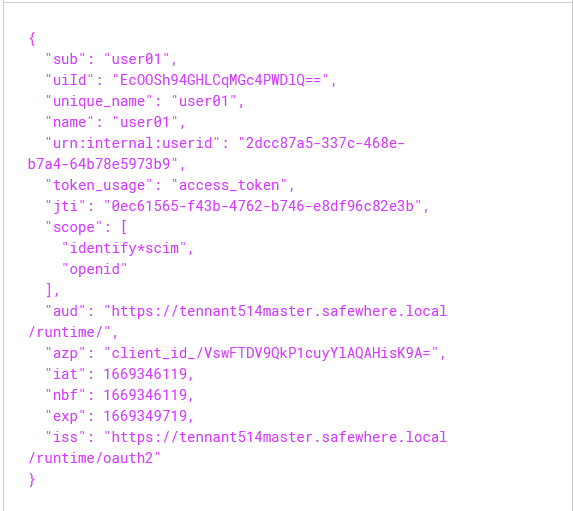
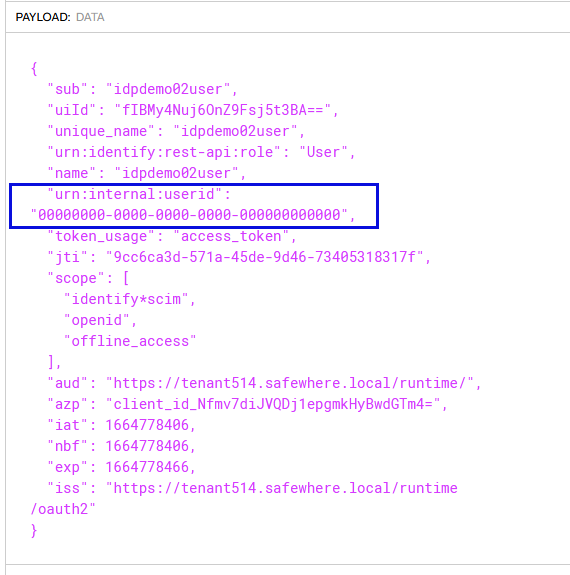
-
The token has the urn:internal:userid claim but its value is invalid
The Access denied page shows up as in the screenshot below:
Implement session timeout control
Identify now allows administrators to configure session timeout of IdentifyMe. You should specify a value that strikes the right balance between security and usability, so that your users can comfortably complete all required operations within the application without their sessions frequently expiring.
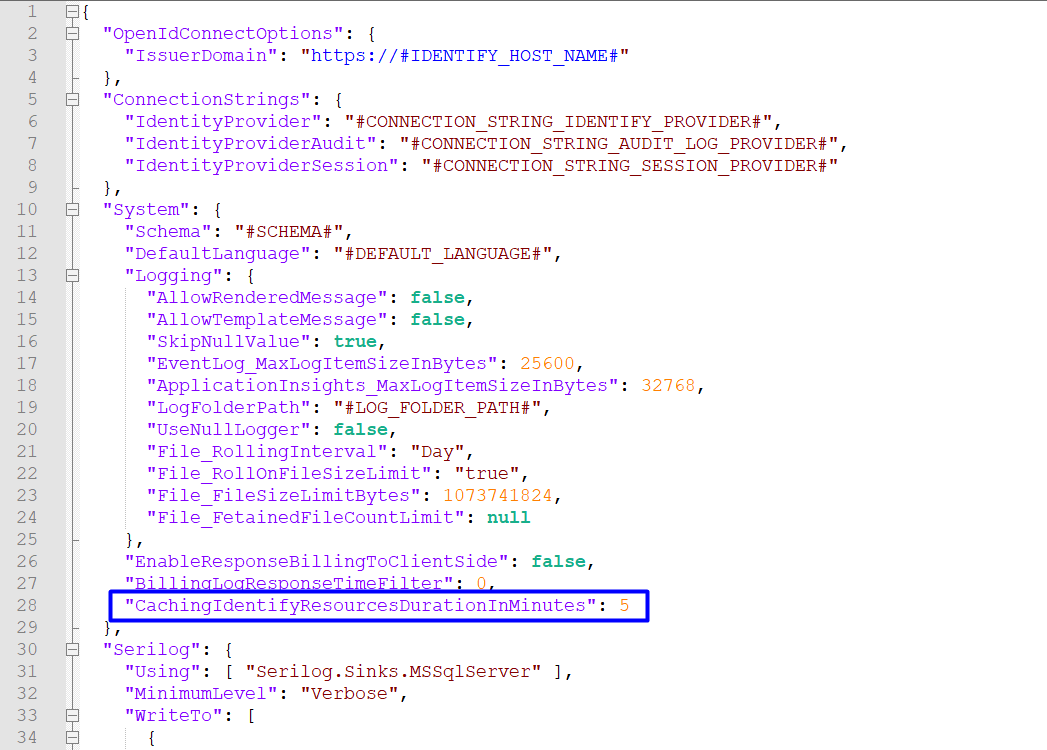
Improve performance by using caching to reduce calls to REST APIs
In 5.14, we have implemented a caching mechanism for IdentifyMe to reduce the number of calls that it needs to make to Identify's REST API. The following data types are cached:
- Claim definitions
- System setup
- Password policy
The default caching duration is 5 minutes. You can customize the caching duration in the appsettings.json file of IdentifyMe:
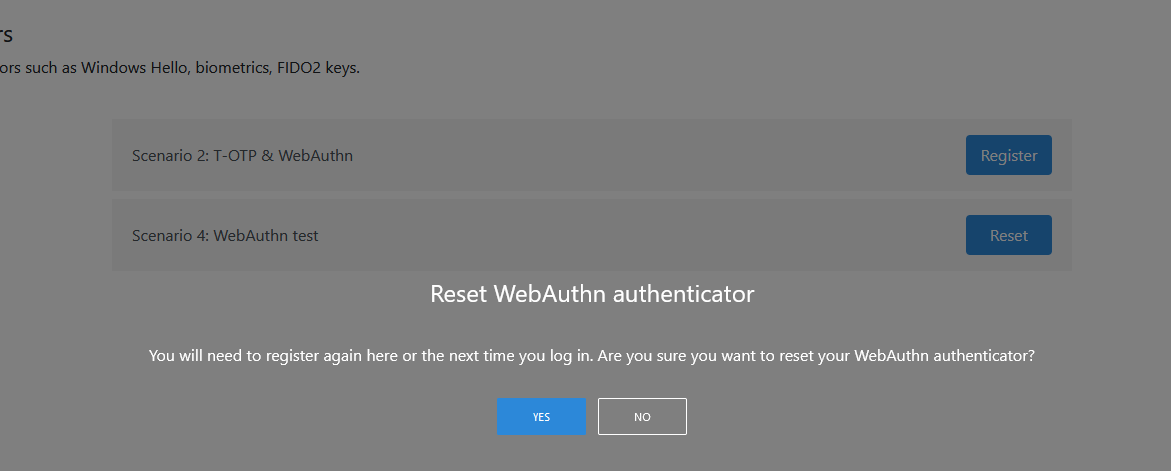
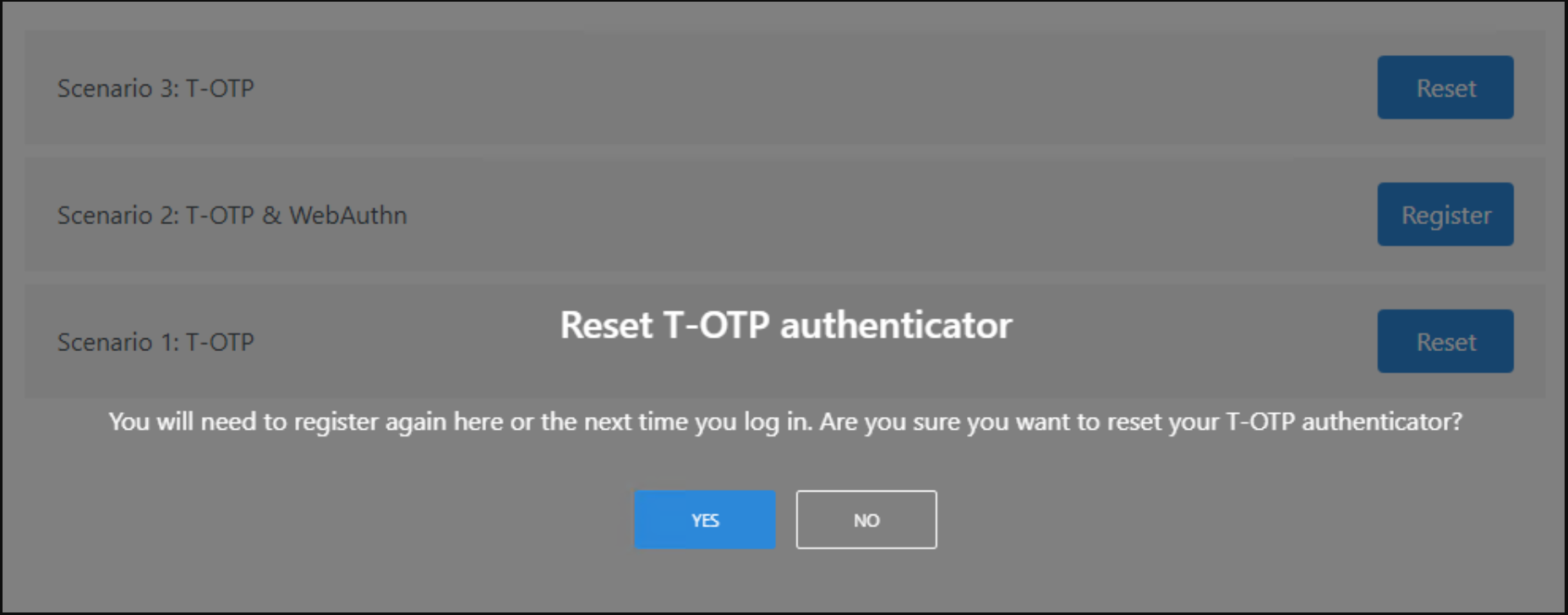
Display a confirmation pop-up when users choose to reset their WebAuthn or T-OTP authenticators
IdentifyMe will show a pop-up to ask users for confirmation after they click on the Reset button.
On the WebAuthn authenticators page:
On the T-OTP authenticators page:
Improve UX of the Error page
A user-friendly Error page will show up when users encounter a problem in IdentifyMe.
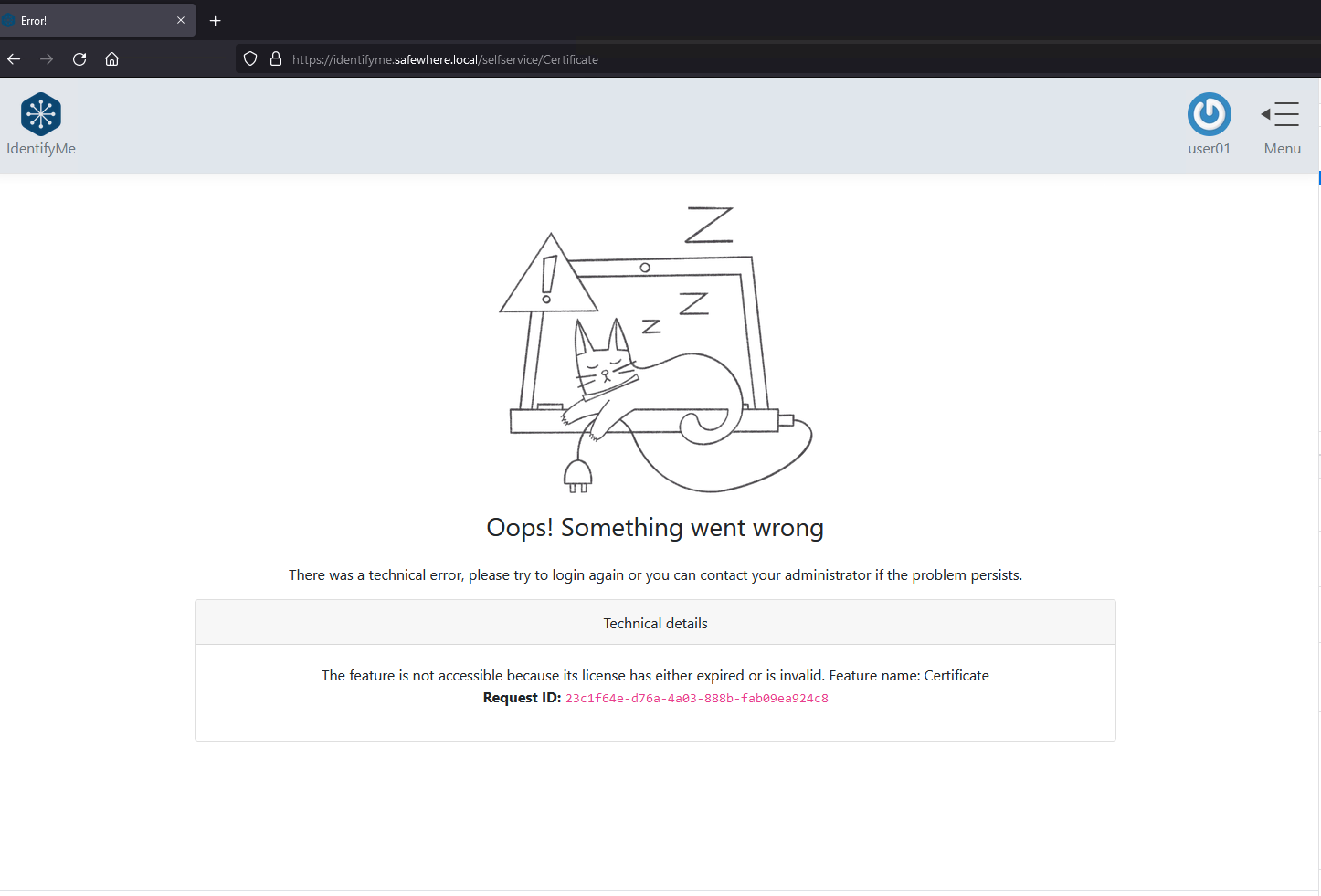
The Technical details section includes extra details about the error when available and a request ID that can help troubleshooting easier.
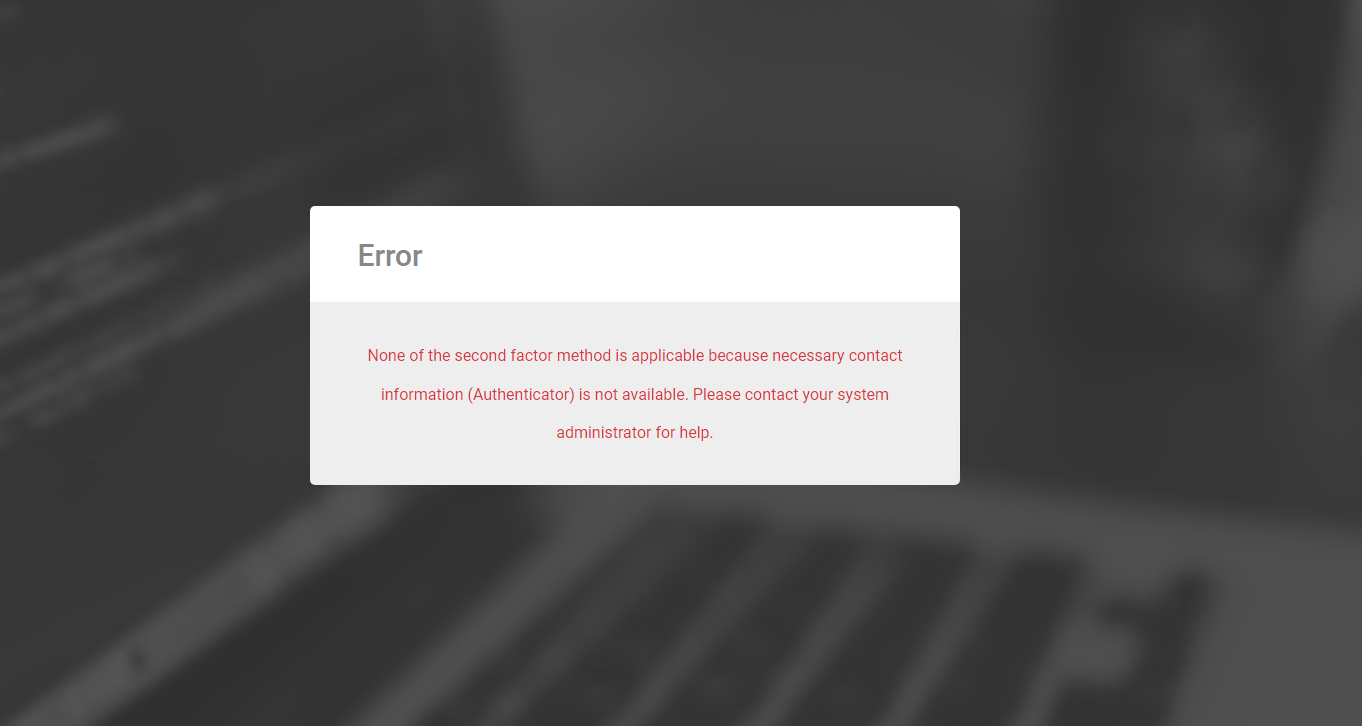
MFA registration when Update unknown users from login is False
In the previous versions, because having an user account in the local user database is mandatory to register an MFA method such as T-OTP or WebAuthn authenticators, Identify required that the Update unknown users from login of an Identity provider must be set to True. However, an installation may have users created in advance, for example by using REST API. In that case, it is actually no need to have that setting set to True. Thus, given that a user needs to register an MFA method, we have implement new business logic:
- If a logging in user has had an account in the Identify local user database already: proceed with registration.
- Otherwise, check the Update unknown users from login setting. If it is set to True, the user can proceed with registration. Otherwise, Identify will show an error as usual.
This improvement is very useful when you do not want users auto-created just to do MFA registration.
Digital Signatures for Safewhere
We start applying Authenticode digital signatures to Safewhere Identify from version 5.14. The Safewhere Identify installer and all code assemblies that are developed and distributed by Safewhere are signed.
When you run the signed installer, you might encounter a SmartScreen warning:
It is because our identity (the in use signing certificate) is new to Microsoft. It will take a while for our installers to build up reputation.
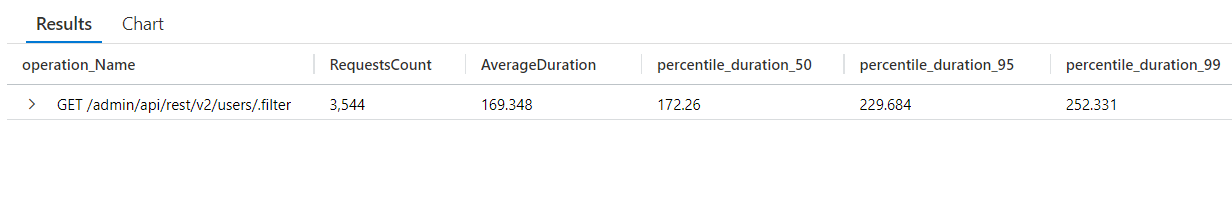
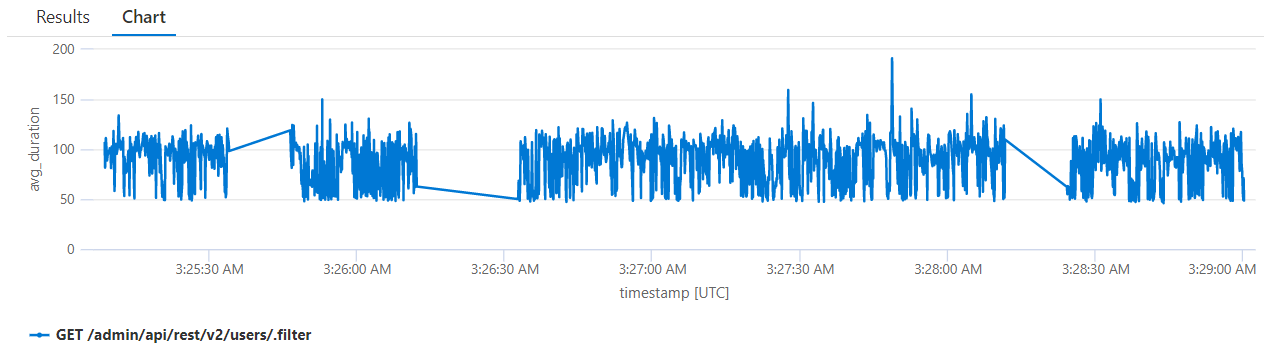
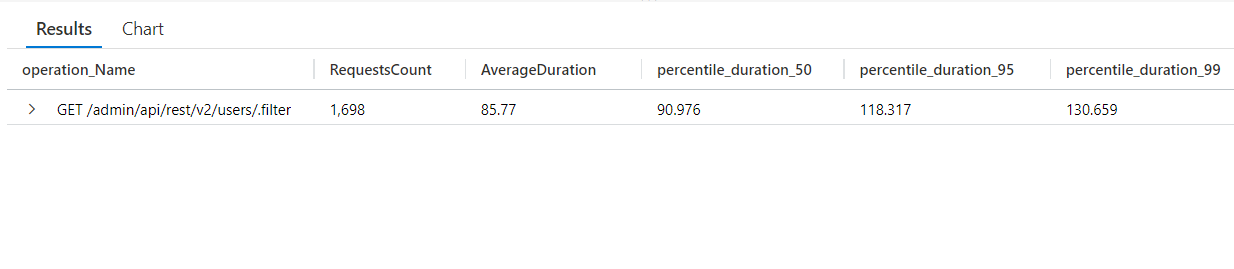
New indices on user's claim tables
We have added 2 new indices to the FreeUserClaimValue and DiscreteUserClaimValue tables which can help improve the performance of activities that need to query those tables such as Username & Password logins and REST API's User filter endpoint.
Before 5.14:
From 5.14:
New indices for the Logs table and other Audit tables
The IdentifyAudit database can contain a large amount of data and having necessary indices is essential for querying data efficiently. You can find list all added indices here.
WARNING: If you have been log data to the Logs table instead of flat files or other log target, we strongly recommend you to run the change script to create all indices before upgrading to Identify 5.14.
Use .NET's built-in validator to do certificate revocation checks for OCES certificates
You can now use .NET's built-in revocation validator to validate OCES certificates. The following table shows what validator is used under various configuration:
| Certificate type | Use database certificate revocation checks | Certificate validation full offline mode enabled | Validator applied mode |
|---|---|---|---|
| Non-OCES certificate | True | False | Database validator |
| Non-OCES certificate | True | True | Database validator |
| Non-OCES certificate | False | False | .NET built-in validator |
| Non-OCES certificate | False | True | .NET built-in validator |
| OCES certificate | True | False | Database validator |
| OCES certificate | True | True | Database validator |
| OCES certificate | False | True | .NET built-in validator with FullOffline mode |
| OCES certificate | False | False | .NET built-in validator |
For troubleshooting purpose, debug logs can tell you what type of validator is used.
Validate signature of ID tokens returned from OAuth 2.0/OIDC Identity providers
After Identify receives an access token from an upstream OAuth 2.0/OIDC Identity provider, it uses the access token to call an endpoint of the Identity provider to get additional user data. That call ensures that the access token must be valid. From version 5.14, Identify also verifies the signatures of ID tokens returned from the providers. You can find more details on this topic
Our new code tries it best to figure out the correct keys that it can use to verify signatures. However, it might fail to do so if you have configured your connections manually in an unexpected way. We recommend that you should test version 5.14 carefully on a test environment before using it on production.
Other improvements
Some other small improvements are:
- Fixed a race-condition issue that could cause SYS logs to not write some log events under a specific logging configuration and load condition.
- Re-added a missing STS request event: Log issuer's thumbprint when a request uses an invalid bootstrap token's trusted issuer.
- Re-added a missing STS request event: Log username value when a request failed to authenticate.
Safewhere Admin
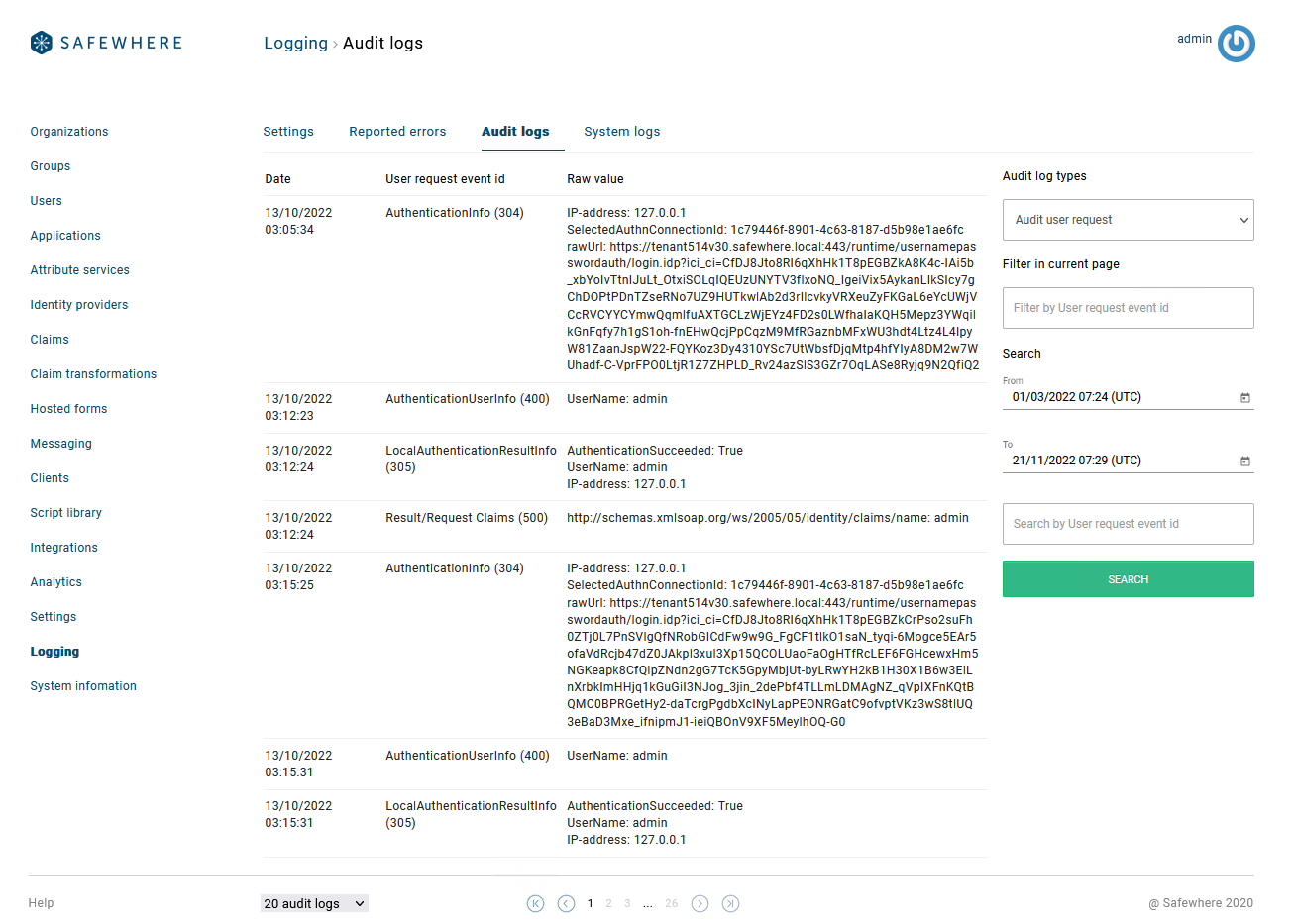
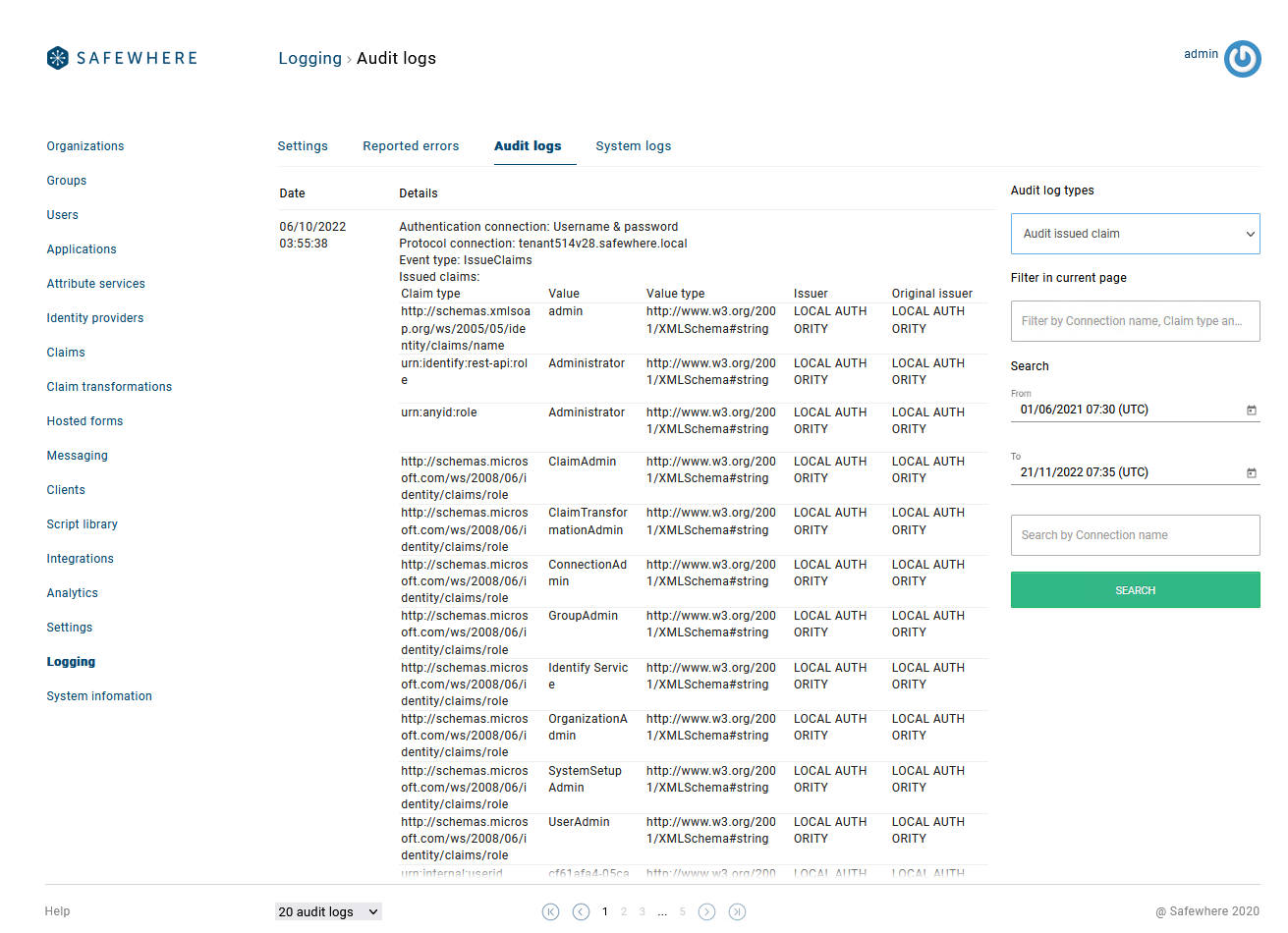
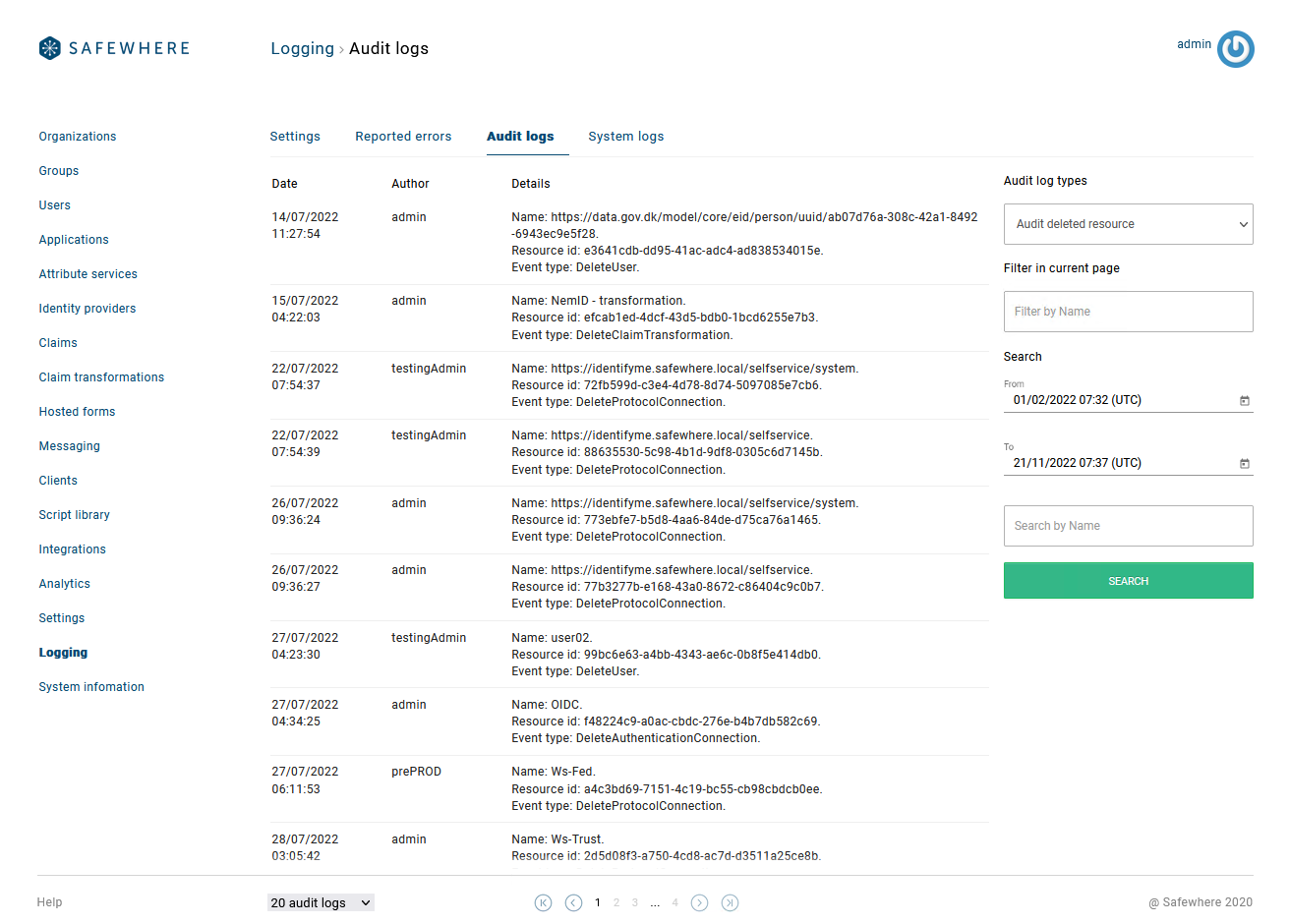
Show more information on Log viewers
You can see more details directly on the list view of the following Audit log viewers:
- Audit user request
- Audit user updated
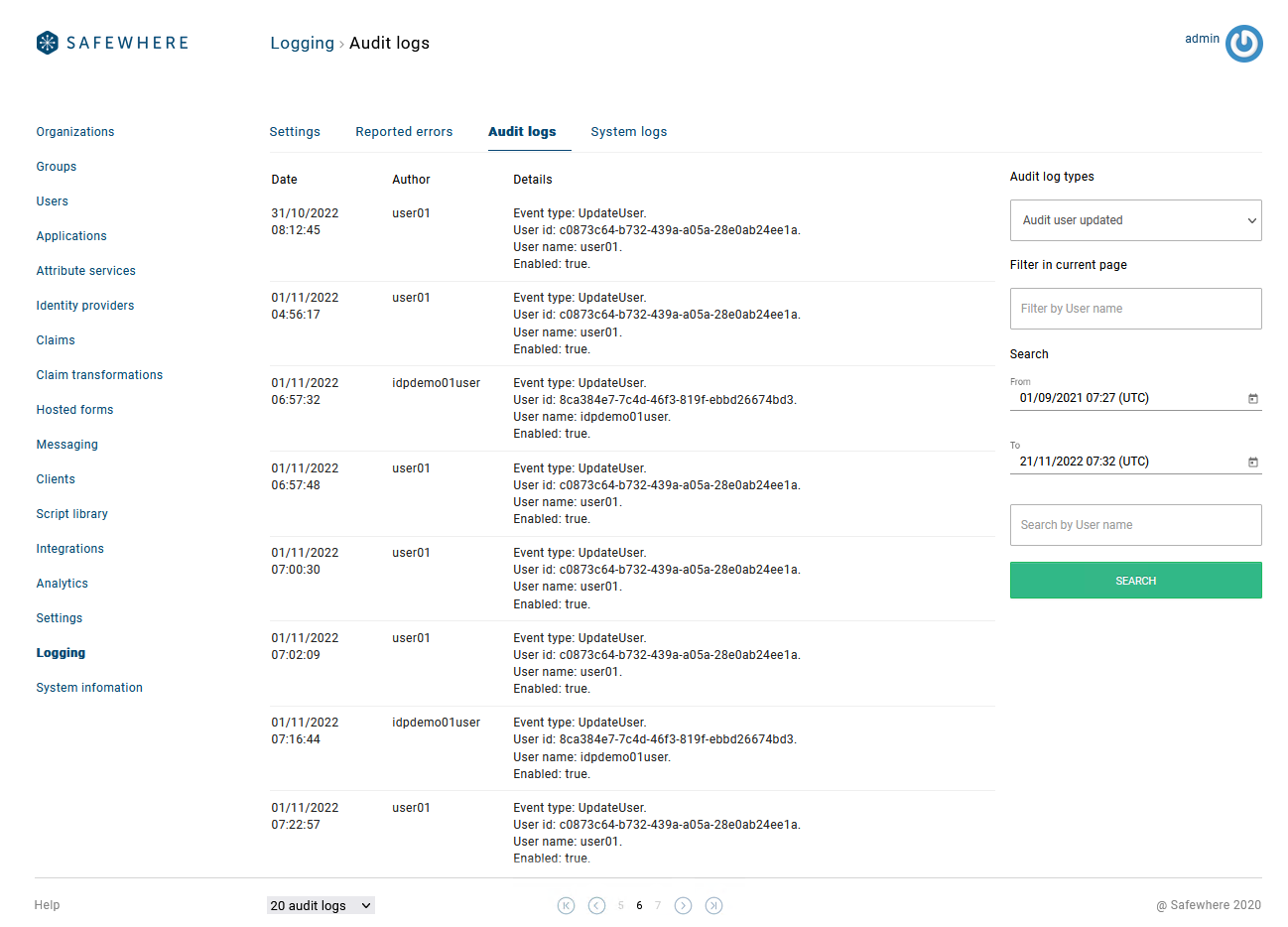
- Audit user created.
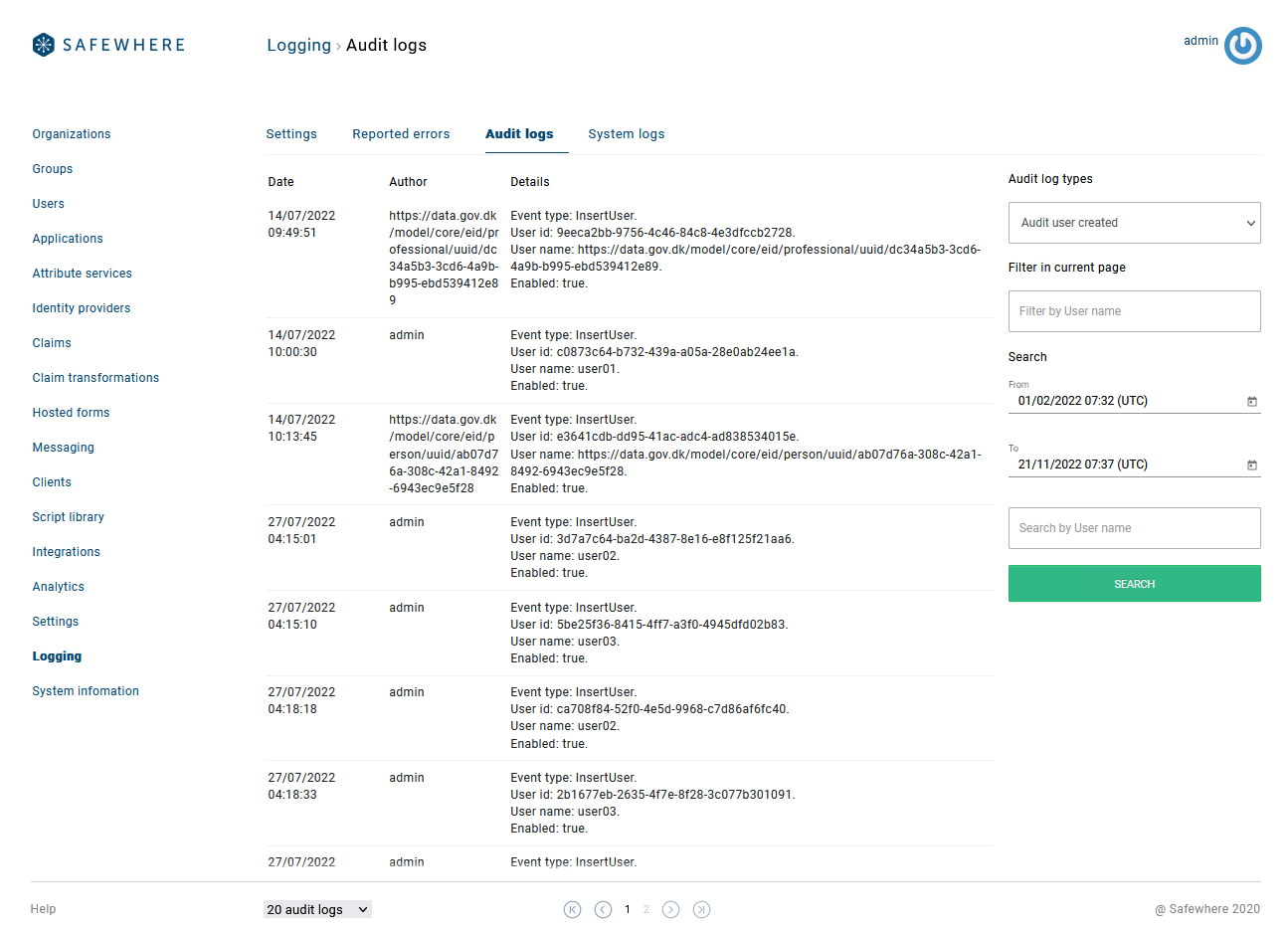
- Audit issued claim
- Audit deleted resource
- Audit user claim
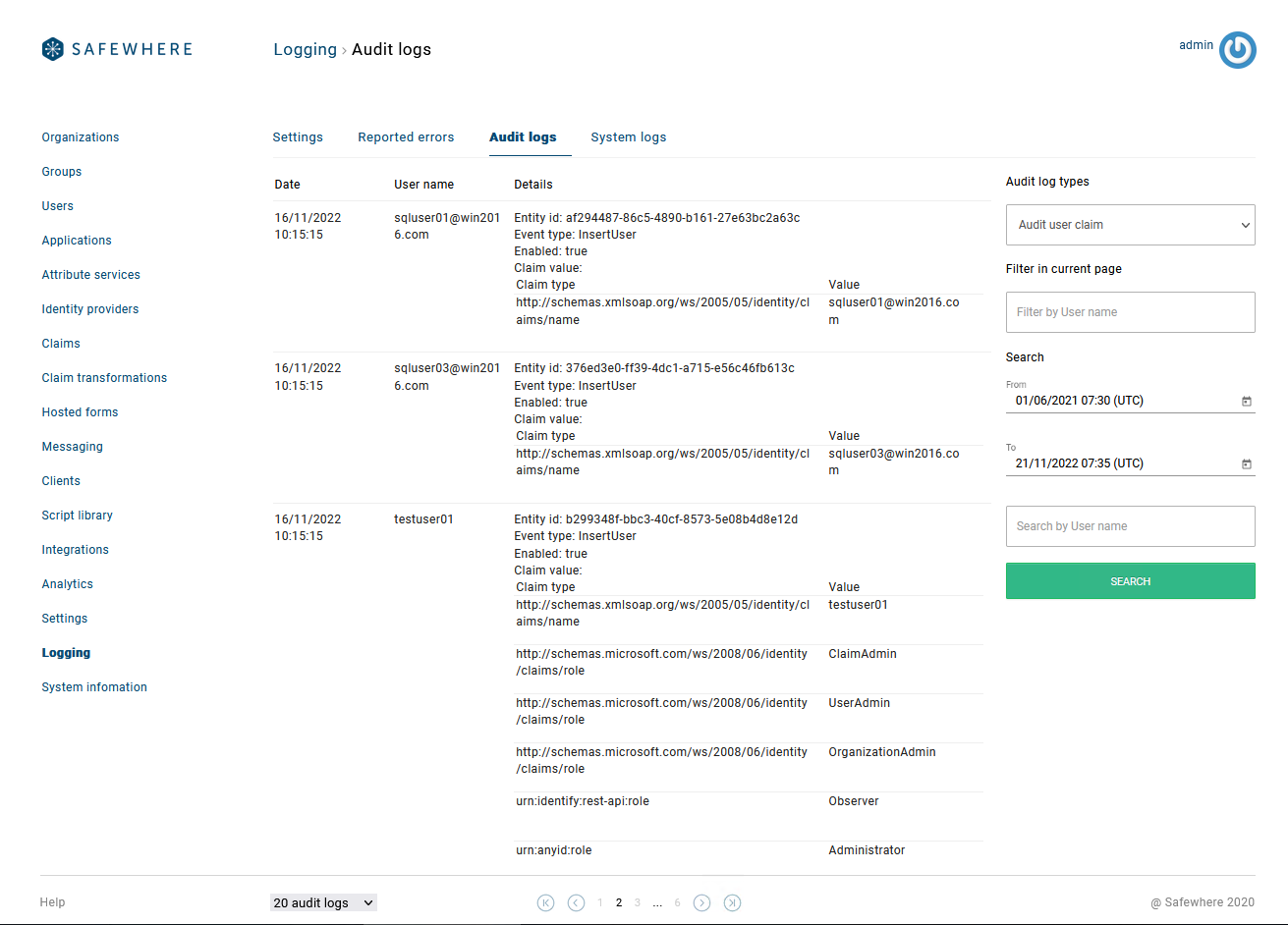
Show more certificate details on the certificate list
You can see more many more details of a certificate directly on the certificate list view: Subject, Thumbprint, Valid from, Valid to, Issuer, Is valid. Addition, you can now search for certificates by Thumbprint (exact comparison) or Subject (contain comparison).
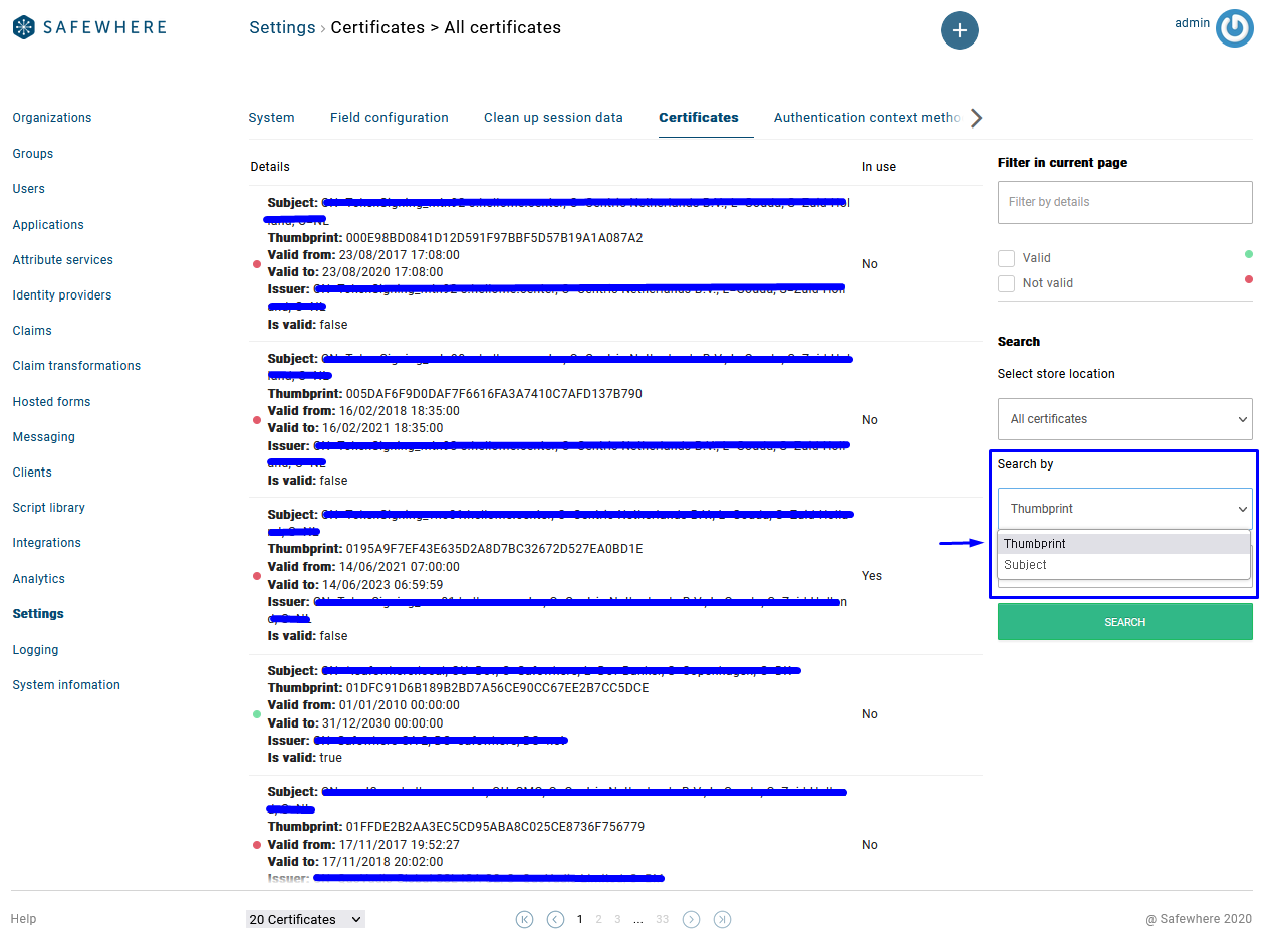
Import custom claim definitions using XML format
We have ported the feature to import custom claim definitions stored in an XML file from the old Admin interface to the new one.
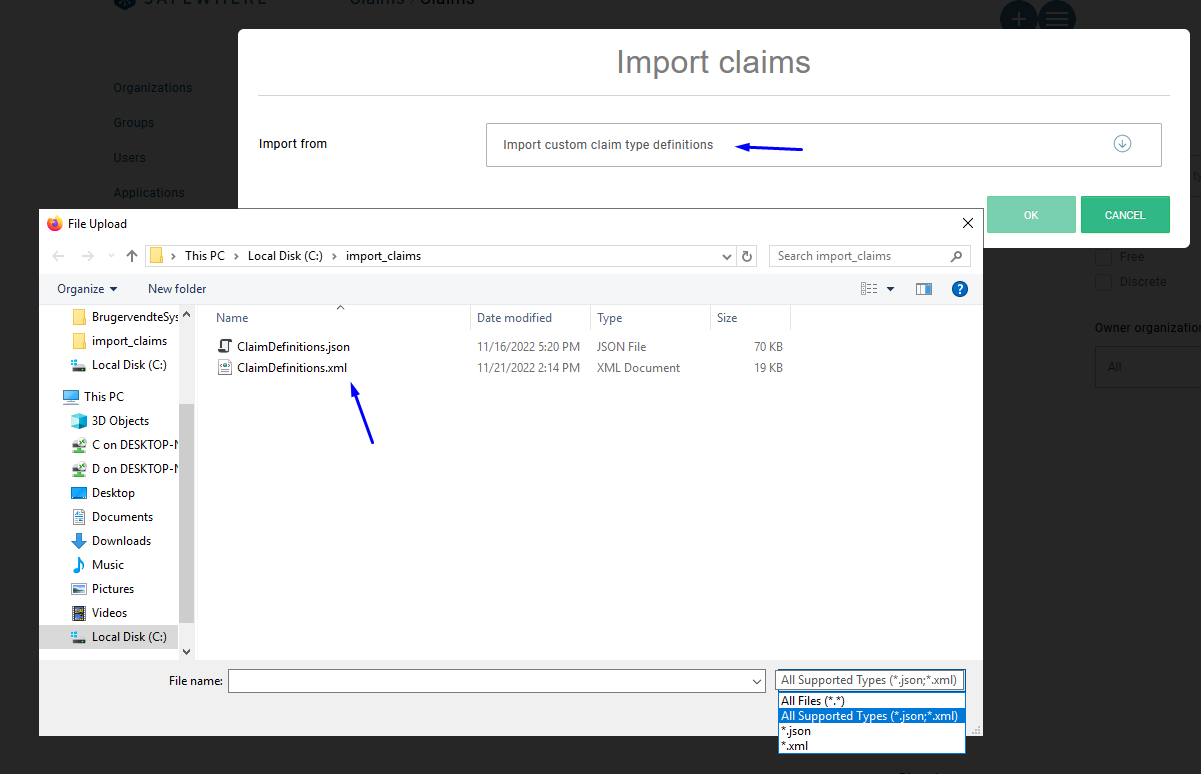
This type of import allows you to select what claim sets to import.
Search by display name on the user list
You can now search for users by display name:
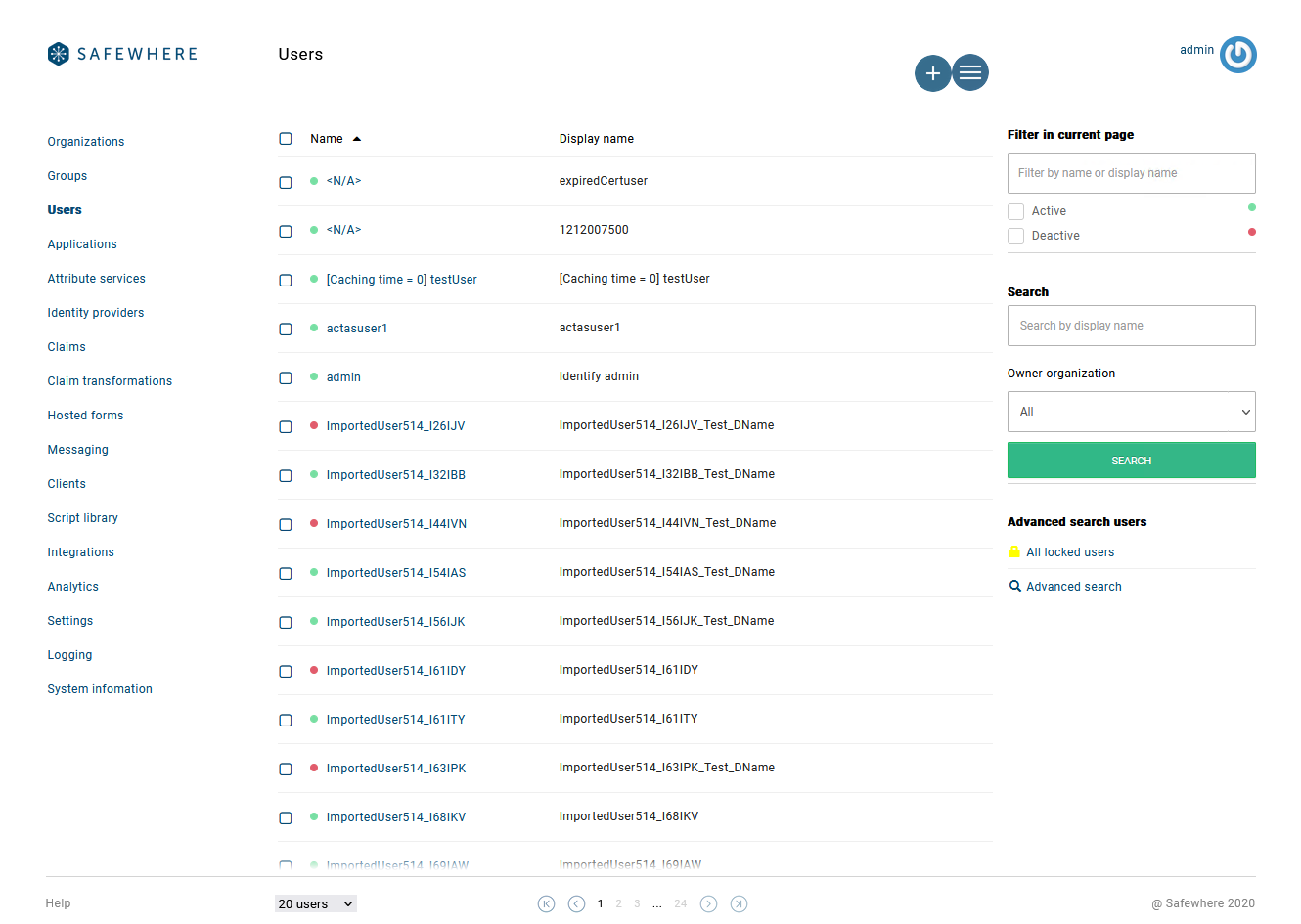
Please note that the Search functionality always looks for users from the whole dataset (aka server-side search), while the Filter functionality only applies to the current page (aka client-side search). We also updated labels of the data columns of the User list to make them consistent to the labels used on the User details page.
Breaking changes
When upgrading Identify instance from a previous version, you may experience some changes:
- The validation of signature of ID tokens returned from OAuth 2.0/OIDC Identity providers feature might fail if your Identity providers have invalid settings.
- You must update jwksEndpoint information on Generic OIDC provider or Social provider JSON data here before you import it to the Identify instance using version 5.14.
Changes in Razor views and Hosted forms
The Enable Authenticator, Enable Device Authentication, Login With Authenticator, Onboarding succeeded, Recovery code and OTP Authentication templates are updated due to bug fixes. Please refer this pull request pull request for more details about the changes. If you are using these forms, you should back them up, then click RESET TO DEFAULT button to view the new templates.
5.14 REST API change
You can find new changes on 5.14 APIs here.
5.14 known issues
You can find known issues of version 5.14 here.
Bug fixes
- Fixed: #88036 [IC] Backup database is ticked as default on Identify configurator.
- Fixed: #88043 [SWadmin] The error page shows values of the well-known claims although they are marked as sensitive claims
- Fixed: #91174 [IC] The alg header and the kid header of access tokens which Identify configurator uses do not follow JSON Web Algorithms.
- Fixed: #91408 [IdentifyMe] Improve UX of multiple discrete claims on My profile page.
- Fixed: #91422 [Runtime] Object reference not set to an instance of an object is returned after a user finishes a tenant upgrade then revisits the /adminv2 application on current browser.
- Fixed: #91686 [SWAdmin] Can rename the IdentifyMe and Identify runtime connections on the Application list.
- Fixed: #91701 [REST API][emailservers] Port number input validation is missing.
- Fixed: #91800 [SWAdmin] Text resources of the IdentifyMe's features are missing on the License tab.
- Fixed: #92012 [IdentifyMe] Cannot register WebAuthn authenticators when the WebAuthn name contains special characters.
- Fixed: #92551 [IdentifyMe] Users cannot save information in My Profile page when they do not input values to all displayed claims.
- Fixed: #93218 [Logging][STS] STS' log events are not logged to Serilog when the UserId field's length has more than 64 characters.
- Fixed: #93348 [OTP] User does not receive a new OTP code when he requests a new OTP code after inputting wrong OTP code many times.
- Fixed: #93503 [SWAdmin] Cannot rename an existing claim transformation with a new name that only has changes in letter case.
- Fixed: #93582 [Logging][STS] SEC Event Ids - 5600, 5604 are missing and EventID 5605's log message is truncated on ActAs run.
- Fixed: #93658 [TrustedBrowser] Additional trusted browser registration page does not display for the old browser right after user chooses to reset his second factor method.
- Fixed: #93727 [SWAdmin] Remove the search by description functionality of the application list.
- Fixed: #93730 [SWAdmin] Add search by category functionality to the Identity provider list.
- Fixed: #96088 [SWAdmin] User is navigated to My Profile page right after renaming a specific application.
- Fixed: #93553 [SWAdmin] The pagination section displays on the claim/claimsets list when user chooses to search claims/claimsets by Organization.
- Fixed: #93421 [SWAdmin] The 'Offer remember user choice of identity provider' always displays in spite of not choosing the Persistent cookies HRD.
- Fixed: #93789 [Runtime] The option Remember my selection keeps showing on the authentication methods list when offerRememberUserChoiceOfIdentityProvider is true and Persistent cookies is removed from the dropdown list of HRD rules.
- Fixed: #96224 [REST API] POST /api/rest/v2/users/onboardauthenticator - User can use secret code of TOTP Authenticator to onboard WebAuthn authenticator.
- Fixed: #93402 [SWAdmin] The Date column on My Profile\History is not sorted as default.
- Fixed: #93421 [SWAdmin] The Offer remember user choice of identity provider displays although Persistent cookies is not selected on the dropdown list of HRD rules.
- Fixed: #88132 [OTP] Internal server error has returned on Identify when user double-clicks on OK button to submit his OTP code.
