Given that both client certifificate and server certificate on LDAPWS which is inuse by ADFSxLogin have expired.
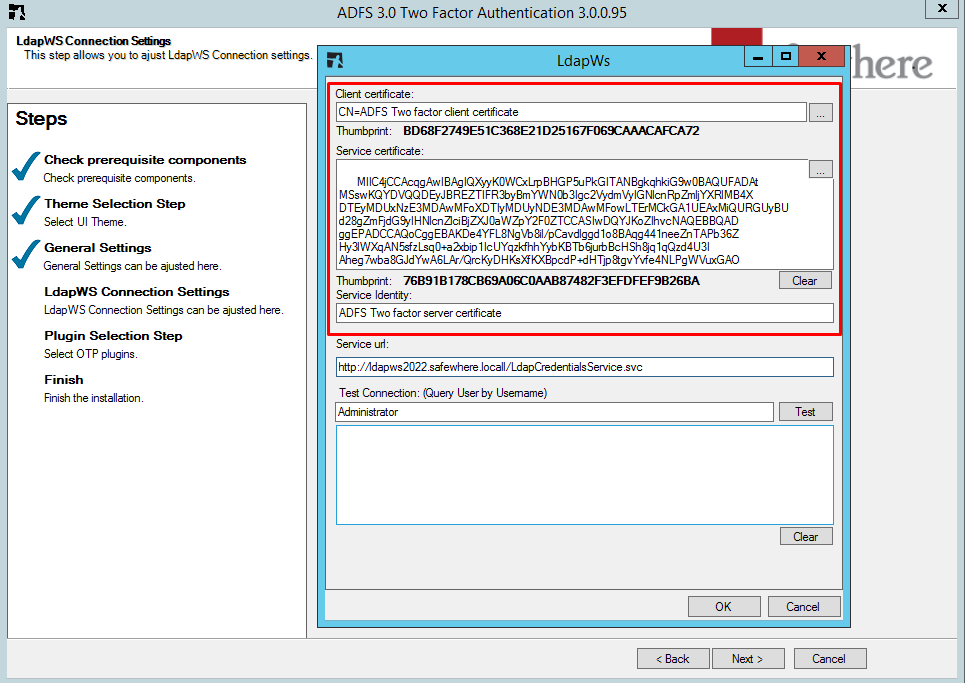
Above wizard does not allow you to access service any longer. You can do:
Certificate preration
- Generate two new certificates which are used as client certificate and server certificate for LDAPWS. In this sample, you can clone two self-signed certificates with Powershell from the currrent ones.
|
1 2 3 4 5 |
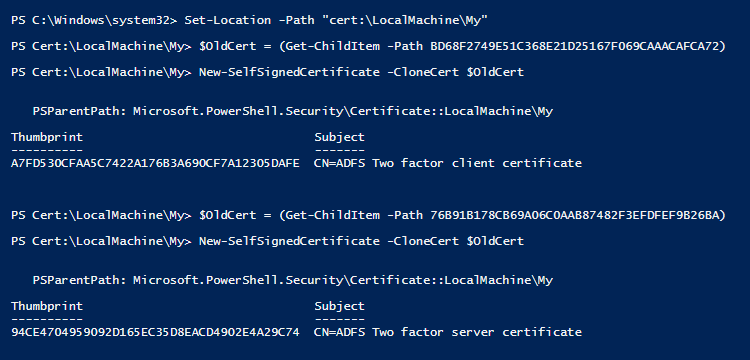
PS C:\Windows\system32> Set-Location -Path "cert:\LocalMachine\My" PS Cert:\LocalMachine\My> $OldCert = (Get-ChildItem -Path BD68F2749E51C368E21D25167F069CAAACAFCA72) PS Cert:\LocalMachine\My> New-SelfSignedCertificate -CloneCert $OldCert PS Cert:\LocalMachine\My> $OldCert = (Get-ChildItem -Path 76B91B178CB69A06C0AAB87482F3EFDFEF9B26BA) PS Cert:\LocalMachine\My> New-SelfSignedCertificate -CloneCert $OldCert |
- Open the certificate store:
- Verify Read permission access to the private key of two new generated certificates are as same as the expired ones. Remove the expired certificates from LocalMachine\My store.
- Export the public keys of two new generated certificates and import them to LocalMachine\Trusted Root Certificate Authorities.
- Import the public key of client certificate to LocalMachine\Trusted People.
Update new certificates on LDAPWS
- Access
C:\Program Files\Safewhere\LdapWS\Tools\LdapConfiguration.xml, change the new thumbprint of service certificate in its tenant XML content.
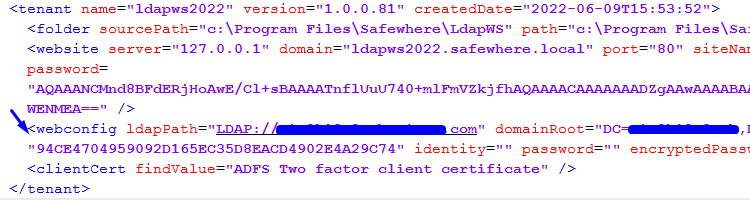
- Access
C:\Program Files\Safewhere\LdapWS\Tenants\#LDAPWSname\web.config, change the new thumbprint of server certificate in-ServiceServersection.
|
1 2 3 4 5 |
<LdapService> <ServiceServer> <ServerCertificate storeLocation="LocalMachine" storeName="My" findType="FindByThumbprint" findValue="94CE4704959092D165EC35D8EACD4902E4A29C74"/> </ServiceServer> </LdapService> |
- Reset LDAPWS application pool or reset IIS.
- Execute the ADFSxLogin wizard again. Fill new certificate thumbprint values and press Test.
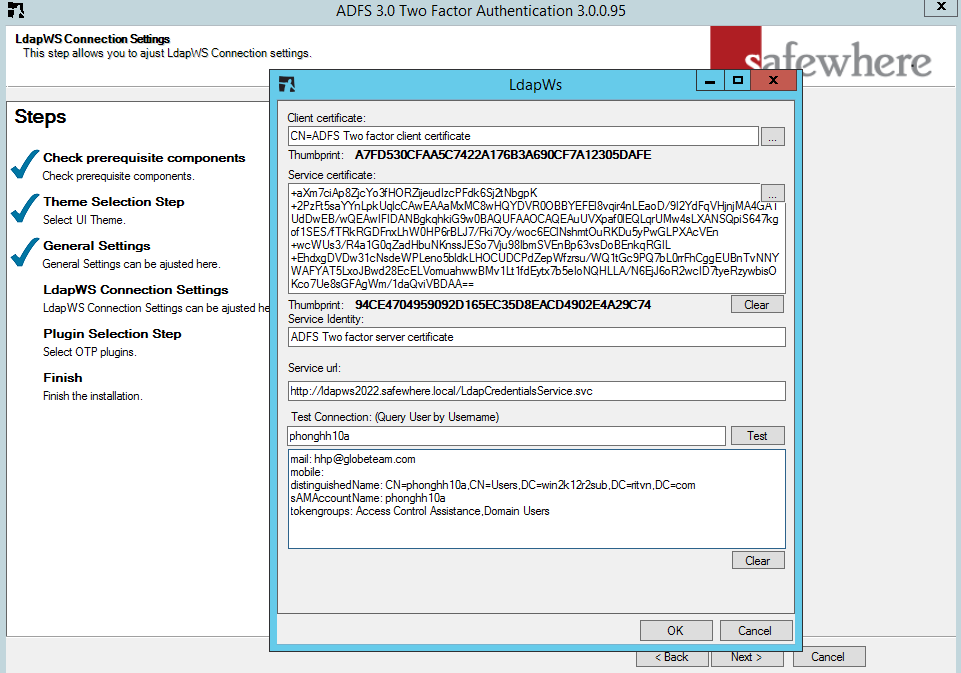
Note: Support for LDAPWS flow has been deprecated since version 3.0.0.208. ADFSxLogin only supports LDAPDirecAccess on LDAP connection method.
