This page will describe all security options that you can configure for your OAuth 2.0 and OIDC Identity Provider connections.
IdToken validation
When processing IdToken
- The token's lifetime is valid.
- The token's audience is valid by matching it against the in use connection's Client Id.
- The token's signature (JSON Web Signature - JWS) is correct.
- When
RSASigningis used and when the in use signing certificate is found in thex5c
In the next sections, you will learn more about all validation settings and how the Social and Generic OIDC Identity providers do validation.
Generic OIDC providers
Settings
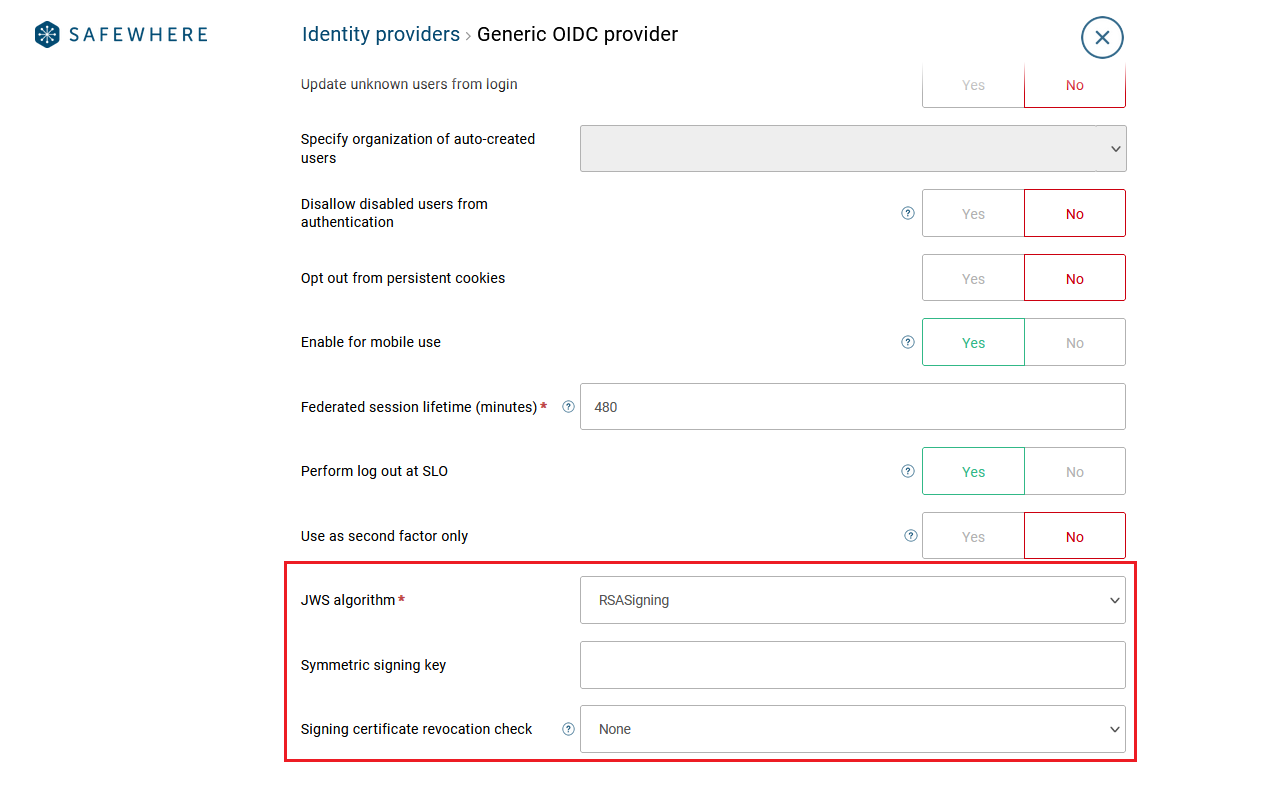
For a Generic OIDC provider, you can use the following settings to control the JWS
Tip: You can just specify the URL to the well-known configuration endpoint and Identify will fetch all the other endpoints (URLs) for you.
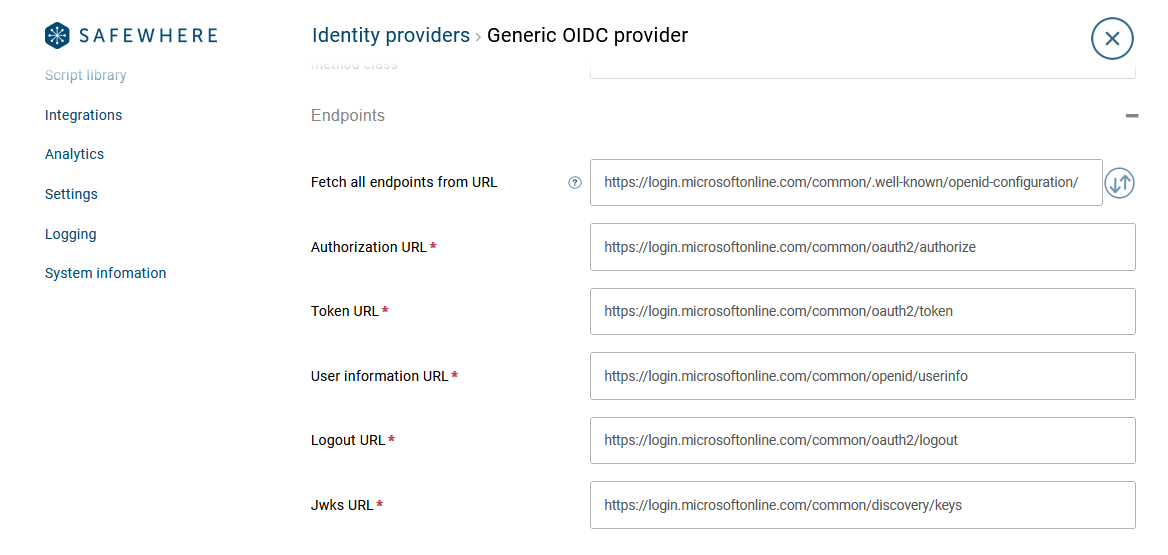
- Jwks endpoint: Identify fetches the signing certificate chain which it uses to validate signatures of
IdTokenwhen theRSASigning - JWS Algorithm: specifies what algorithm that the OIDC provider uses to sign the
AccessTokenandIdToken. Supported values areRSASigning,HMACSymmetric, andNone. TheNone - Symmetric signing key: specifies the Symmetric signing key that the OIDC provider uses to sign. This setting is required if you set the
JWS Algorithmsetting toHMACSymmetric - Signing certificate revocation check: Signing certificate revocation check mode to validate the signing certificate that the OIDC provider uses to sign tokens. You can select the
None
You must set a correct Jwks URL or fetch it from the .wellknown/openid-configuration
Social OIDC providers
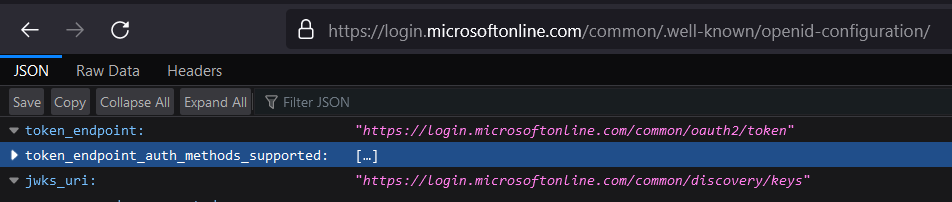
Some social OIDC providers such as Microsoft provides a JSON Web Key Set endpoint which can be found in their discovery endpoints: .wellknown/openid-configuration. All of these social OIDC providers are using the RSA algorithm to sign the IdToken
An example of discovery endpoint and JSON Web Key Set (Jwks) from the Microsoft is:
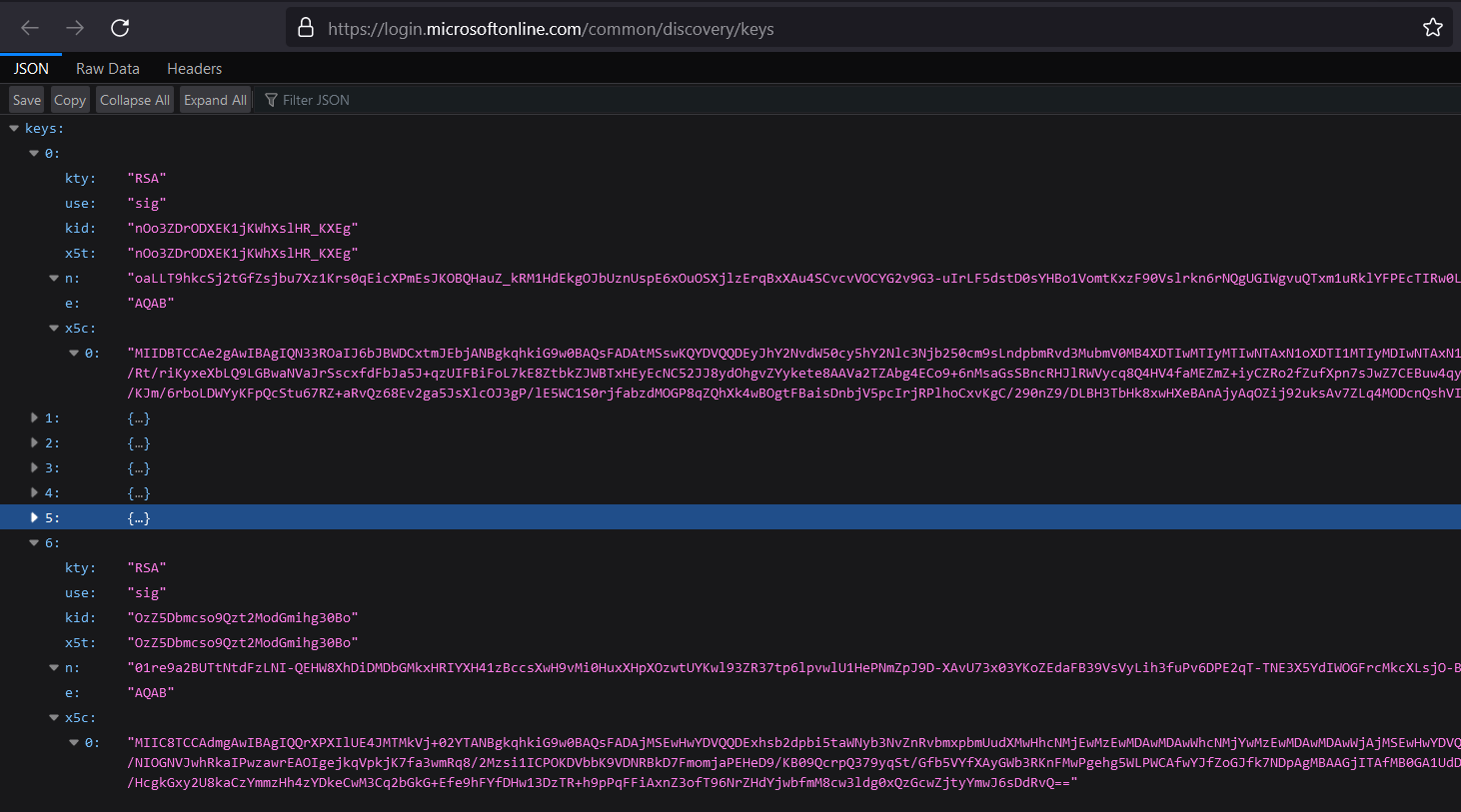
The state of validating signing certificates of Social providers is:
- Microsoft: both signature validation and certificate validation are done.
- Facebook, and Google: only signature validation is done. No certificate validation is done because they do not provide the
x5ccertificate chain. - Twitter: no validation is done because Twitter does not implement OIDC like other providers.
- LinkedIn: LinkedIn has implemented a new authentication solution. We will update Identify to use the new one in version 5.15.
Validation result
A failed validation stops a login.
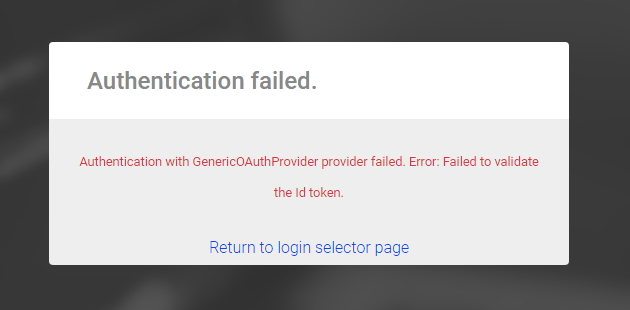
For both successful and failed cases, Identify logs a corresponding SEC log event:
- Successful validation: Event Id 4117
- Failed validation: Event Id 4116
