Safewhere Identify 5.7 Release Notes
This document summarizes all new features and bug fixes for version 5.7 as well as breaking changes when being upgraded from previous versions.
New features and improvements
Identify Configurator
Identify Configurator CLI
In version 5.7, we implemented a very powerful feature called Configurator CLI which is a command-line interface of the familiar Configurator UI. The CLI supports most of the functionalities that you can find in the UI such as:
- Provision an instance.
- Reconfigure an instance.
- Import and export data.
The CLI tool is shipped with Safewhere Identify installer so no additional installation is required. You can refer to Configurator CLI Overview for more details.
Note: when creating / upgrading an Identify instance, CLI will automatically deploy Safewhere Admin if it has not been deployed before. We will retire the old Admin interface soon so the new Admin interface has become mandatory now.
New setting: Required Server Name Indication
You can now set the Required Server Name Indication from the Identify Configurator UI when creating a new Identify instance instead of having to use the IIS Manager. (Note: This option is only available from IIS 8.0). The Identify CLI also has support for this new setting.
New setting: Idle Time-out (minutes) for the Safewhere Admin Application Pool
The Idle Time-out (minutes) value for the Safewhere Admin Application Pool in IIS can be set when creating or upgrading Identify instance.
Export/Import users' data (a.k.a backup/restore users' data) with password hash and salt
In the previous version, because you couldn't export users' passwords, when you import the users into a destination tenant,
you would need to type in passwords for every single user manually.
The configurator tool can now export users with their password hashes and salts and import them to a destination tenant.
We also add a guideline for how to do data migration from an instance of an old version to an instance of the latest version.
Deploy Safewhere Admin when upgrading an Identify instance
In the previous version, you need to use the re-configure feature to install the Safewhere Admin for an existing instance. That additional step might be a problem if you have a huge amount of instances to upgrade. In this version, we provide an option to deploy Safewhere Admin when doing a normal upgrade. In addition, in order to save you some precious server memory, we a also ship a new setting that allows you to shut Safewhere Admin down when it is no longer needed. You can refer to deploy Safewhere Admin when doing upgrade for more details.
Support custom folder for installation
In the previous version, you have to update some settings in the app.config file manually when installing Safewhere Identify in a custom folder. In this version, we fixed the issue so that you don't have to do the manual steps anymore.
Application insights support
Azure application insights (AI) is a great tool to monitor operations of Safewhere Identify and from this version we implemented it for Identify. You can refer to monitoring application insights for the user manual.
OAuth/OIDC 2.0
OIDC compliance
We tested Identify against the OIDC official compliance tool and made a few changes to fix compatibility issues:
- Dynamic registration supports more options on the response_types parameter.
ID token contains the user claims
Currently, the users' claims are added to the Access Token and the UserInfo's response. However, in some cases, our customer wants the user claims to be in the ID token instead. You can now use a new option to control whether the user's claims should be put in Access token or the ID token. You can refer to User claims placement setting for more details.
OP Compliance - RP-Initiated OP
We added support for more validations on the end_session_endpoint which are required by the OP Compliance profile.
response_types parameter on the dynamic registration
We added support for the response_types parameter in dynamic registration request.
SameSite cookie
Microsoft pushed out updates for .NET which are supposed to deal with recent changes in the SameSite specification made by Google and Chrome. The changes prevent the browser from sending the Identify cookies which are used in the POST-based-redirect manner along with cross-site requests. Those cookies must use SameSite=None to ensure that all login flows work properly. In addition, we implemented browser agent sniffing which makes our solution work for old browsers that don't support the None option correctly. You can find more information about our solution here.
Saml 2.0 for WIF - SameSite cookie
Our Saml 2.0 for WIF component guidance has tips how to implement support for the Samesite cookie for SAML 2.0 for WIF applications.
MongoDB and CosmosDB support
We have full support of audit logging to MongoDB and CosmosDB. You can access the topic to create a new Identify instance using MongoDB or CosmosDB as its audit logging store.
Identify REST API and Safewhere Admin
Identify REST API
Logging enhancement
We improved error messages returned from the REST API to include more details about what the faulty resources are. For example, we send a POST request to create a connection and one of the dependent connection doesn't exist.
Before:
|
1 |
"Sorry, dependencyConnectionName is not found." |
After:
|
1 |
"The dependency connection named '{0}' is not found." |
GET method on customized database text resources
In this version, we continue to expand the GET method to get text containers and text resources which are stored in the Identify's database. You can find more information about this new feature at Set up and use custom database text resource.
Performance enhancements for Users GET filter REST API
SCIM specification defines sophisticated filters to GET resources. When sending those filters to Identify REST API, filters that are translatable to SQL queries will run faster than ones that aren't. In version 5.7, we have made more GET users filters translatable to SQL queries. You can find examples for such queries in the REST API's Swagger documentation. Some complex filters can run 10x faster than before.
Safewhere Admin
New Organization resource available in Safewhere Admin
You can now add/edit/delete an organization, assign resources to a specific organization or even filter resources based on organization using the Safewhere Admin. You can refer to Safewhere Admin's Organizations for more details.
New Group resource available in Safewhere Admin
You can now add/edit/delete a group or assign users to a specific group using the Safewhere Admin.
A button to copy the Symmetric signing key field to clipboard
We added support for a Copy button next to the down arrow. You can press it to copy the Symmetric signing key value to clipboard.
More advanced settings on the WSFederation Identity provider
You can now set or update "Home realm discovery"/ "Second factor"/"User template" settings when editing a WSFederation identity provider.
Many more features ported from the old Admin interface
We ported many features from the old Admin to the new Safewhere Admin interface:
- User tools: Mass update, Mass update status, Mass delete.
- Users advanced search.
- Claims tools: import predefined claims or custom claims sets.
- Audit logs viewer: A new tab inside the Logging section where an Admin user can view audit logs of user requests, user created events, user updated events. The viewer works for data stored in SQL Server/MongoDB/CosmosDB.
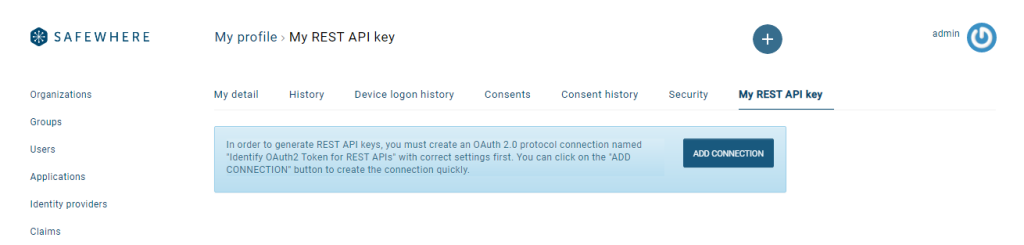
My REST API key from My Profile
You can now generate REST API keys from the new Safewhere Admin interface. However, for security purpose, you need to have the Administrator permission to generate the keys.
Another new nice feature is that if the "Identify OAuth2 Token for REST APIs" connection is not available yet, you can now create it directly from the My REST API key page.
Other improvements
- Paging: Improve paging for resource pages, update icons for the First and Last page and add Next and Previous buttons
- Add Select all and Deselect all (dependency connections) buttons to Applications and Identity providers pages
- Add option "Restrict view and editing of sub-organizations" to the Claims edit page
Bug fixes
- Fixed: #66341 User form - the Edit "username" label is not updated when its Name value is changed
- Fixed: #66342 [SWAdmin] User list - The text color on the Search field makes it too difficult to see its content
- Fixed: #67047 [SWAdmin] UI improvement for Client secret
- Fixed: #67032 [github] Some issues at AspnetWebMvc - JS error when executing the logic flow on the client sample: AspnetWebMvc
- Fixed: #67640 [My REST API key] The claim device-fingerprinting appears in the exchanged access token
- Fixed: #67782 [SWadmin] User can't access any application on the application list
- Fixed: #67639 [Implicit][idtoken token] The access token doesn't contain the email claim when the requested scopes contains "email"
- Fixed: #67729 [SWAdmin] A value is added to the SOAP binding behavior customization when user only adds it on SOAP binding binding customization (it occurred at System setup page/ SAML2.0 application/ SAML2.0 Identity provider)
- Fixed: #67294 [userinfo] The userinfo response doesn't contain any user claims after switching the user claim replacement setting from idtoken to accesstoken
- Fixed: #67035 [OP Compliance] OP-RpInitLogout-Bad_redirect_uri - The error message doesn't stop at the Identify error page
- Fixed: #67036 [OP Compliance] OP-RpInitLogout-Modified-id_token_hint - The error message: Internal server error returns when using an invalid id_token
- Fixed: #67037 [OP Compliance] OP-RpInitLogout-No-id_token_hint - The error message doesn't return when the logout request doesn't contain an id_token_hint
- Fixed: #67997 [Identify] The existing connection "Identify OAuth2 Token for REST APIs" which was created on previous versions doesn't use clientsecrectbasic as its token endpoint authentication method
- Fixed: #67971 [OAuth2] The email values are duplicated on the id_token content when login OIDC flow using id_token /id_token token and the requested scope contains email and User claims placement is id_token
- Fixed: #66940 Wrong fallback when a language code has 3 levels
- Fixed: #68150 [IdentifyAdmin/SWadmin] The index of an authentication connection is not correct when its connection is updated right after it is created
- Fixed: #68098 [SAML2.0] Returned RelayState value of a response to a POST logout request is not correct
- Fixed: #68179 [SAML20 IdP][Uploadmetadata] - The "Use Subject.Name from NameId for identity bearing claim if it exists" and "Transfer domain to upstream Identity Provider" settings are reset after uploading metadata
- Fixed: #68180 [SAML20SP][Uploadmetadata] - The "Run custom Home Realm Discovery rules before static rules" setting is reset after uploading metadata
- Fixed: #68181 [WSFEDIDP][Uploadmetadata]- The interceptor section is reset after uploading metadata
- Fixed: #68182 [WSFEDSP][Uploadmetadata]- Some settings are reset after uploading metadata
- Fixed: #68172 [STS] Generic provider - the login is broken when running a WSTrust connection using a Generic provider connection as its Identity Provider
- Fixed: #68275 [SWAdmin] An error happened when a user tried to log in to the Safewhere Admin then log out using different user accounts a few times
- Fixed: #69285 [Correlation error] When reporting an error using the report error form, database connection strings are logged with credentials in plain text.
- Fixed: #66940 Wrong fallback when a language code has 3 levels
- Fixed: #68205 [SWAdmin][Applications] In SAML application, change the text "Always use authentication context method class" to "Always use default requested authentication context class" and the text "Authentication context class" to "Default requested authentication context class"
- Fixed: #68197 [Monitoring metadata] Stop working in mongoDB
- Fixed: #67845 [SWAdmin]Correct Date Time format text in some pages for being consistent
- Fixed: #67473 [SWAdmin - Group] Should not allow delete Group which is assigned to user
- Fixed: #69740 [IC] Upgrading the replicated tenant including Safewhere Admin is failed
Breaking changes
When upgrading Identify instance from previous version, you may experience some following unexpected issues or changes:
- The existing connection "Identify OAuth2 Token for REST APIs" which was created on previous versions doesn't use clientsecrectbasic as its token endpoint authentication method