Related Posts
Safewhere Identify 5.6 Release Notes
This document summarizes all new features and bug fixes for version 5.6 as well as breaking changes when being upgraded from previous versions.
New features and improvements
Identify Configurator
One of the key feature that we ship in version 5.6 is the import/export data (aka backup/restore data). You can use this feature to export data from one Identify instance and import that data to another instance. The export feature works for Identify instances from version 5.1.1 onwards. However, exported data can vary depending on what REST API is available in what version. Meanwhile, we recommend that you import data to Identify instances 5.6 onwards only because we have tested that use case thoroughly.
OAuth/OIDC 2.0
You can visit OAuth/OIDC's document site for all features and documents that Safewhere Identify can offer.
OpenID Connect Session Management
Even though Identify has had support for OIDC session management from the previous versions, we have updated the feature with more requirements from the latest draft. The feature is now complete.
PKCE for code flow
We have added support for the PKCE option for the code flow grant. We have tested the feature against a web application that has server code. We are testing the feature against browser-based apps and will update result when we are done with it.
Mutiple redirect_uri
You can now configure multiple redirect_uri for a single OAuth 2.0/OIDC connection. This is especially useful when you want to use a single connection for many client apps.
OIDC compliance
We tested Identify against the OIDC official compliance tool and made a few changes to fix compatibility issues:
- Support kid header on id_token
- Support jwks and jwks_uri parameters in dynamic registration request
- Support signing for UserInfo response
- Correct claims on ID Token when no Access Token is issued
- Support pairwise subject identifier
- Support parsing request parameters on authorization request
- [Key Rotation] Support value private_key_jwt for token_endpoint_auth_methods_supported
- Trying to use authorization code twice will result in revoking previously issued access tokens. Because access token is revoked, when a client calls the userinfo endpoint with that access token, Identify will return an error.
- Support authentication type "private_key_jwt" on id token endpoint.
- Updated sample code in Safewhere's GitHub repository to use POST method for logout.
- OP-UserInfo-sig-any: Service provider can register userinfo_signed_response_alg to signal that it wants signed UserInfo returned.
Other bug fixes
Fixed: #62893 [OIDC] Missing the auth_time at the id_token when the authorization request contains the parameter max_age
Fixed: #63700 [OIDC] Re-login unsuccessfully when requesting ID Token with max_age=1
Fixed: #65924 [OAuth] Should return an error response with invalid_request code when the client_id parameter is missing from an authorization request
Messaging
Multi-language email template
Multi-language email template is another cool feature that we are happy to ship in this version. Before, an email template supports a single language. From this version, you will be able to specify multiple languages for a template as follow:
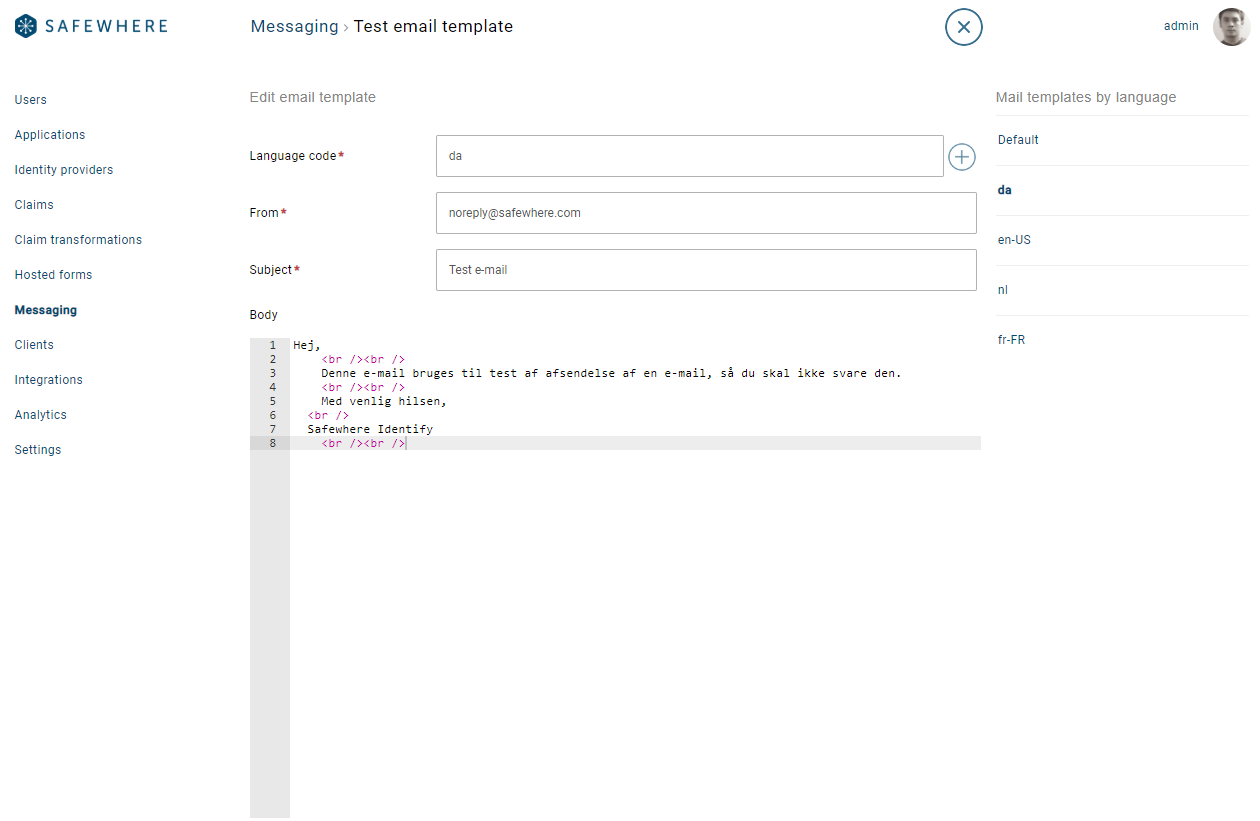
Editing templates can be done by using either REST API or both Admin UI.
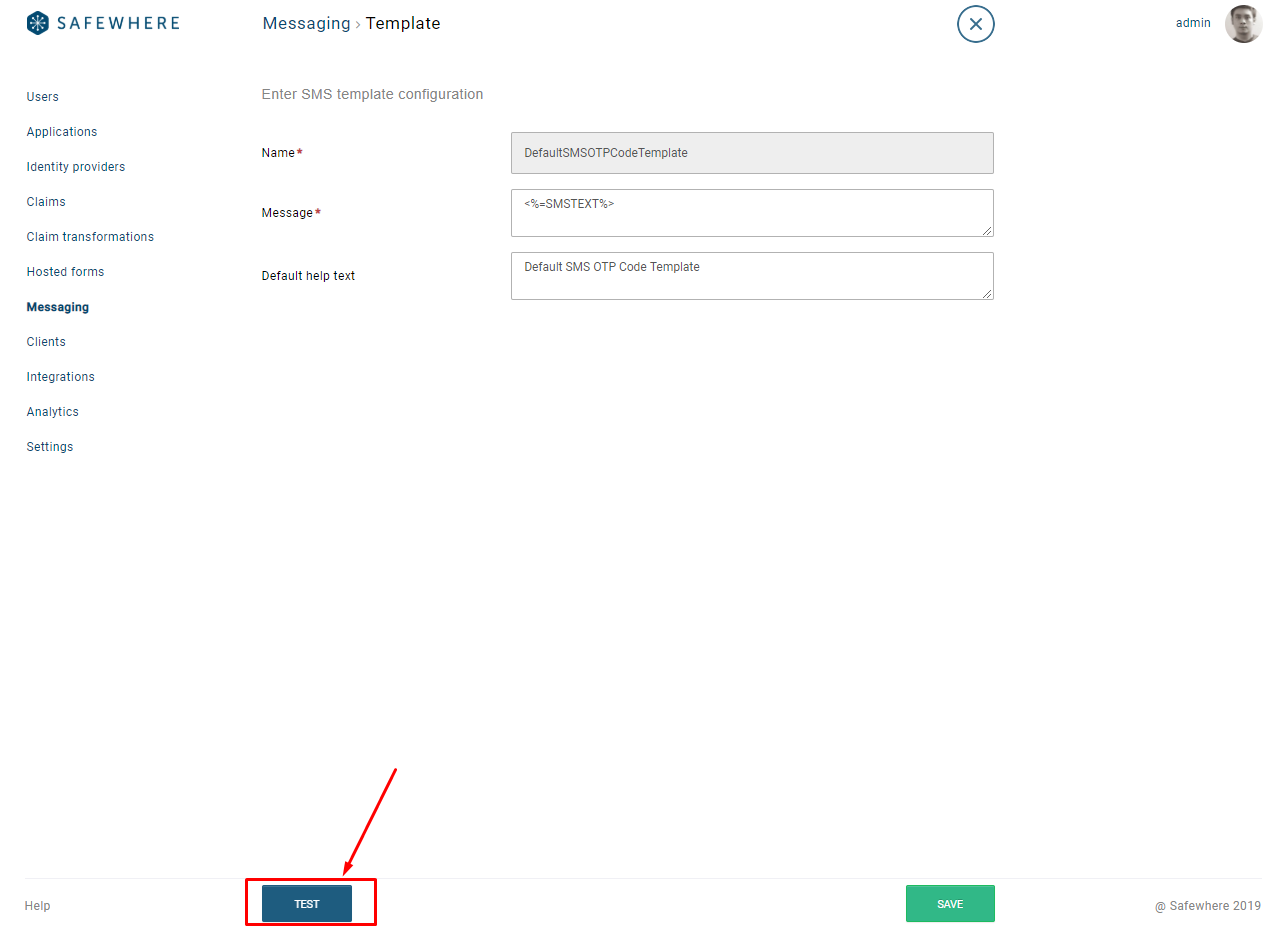
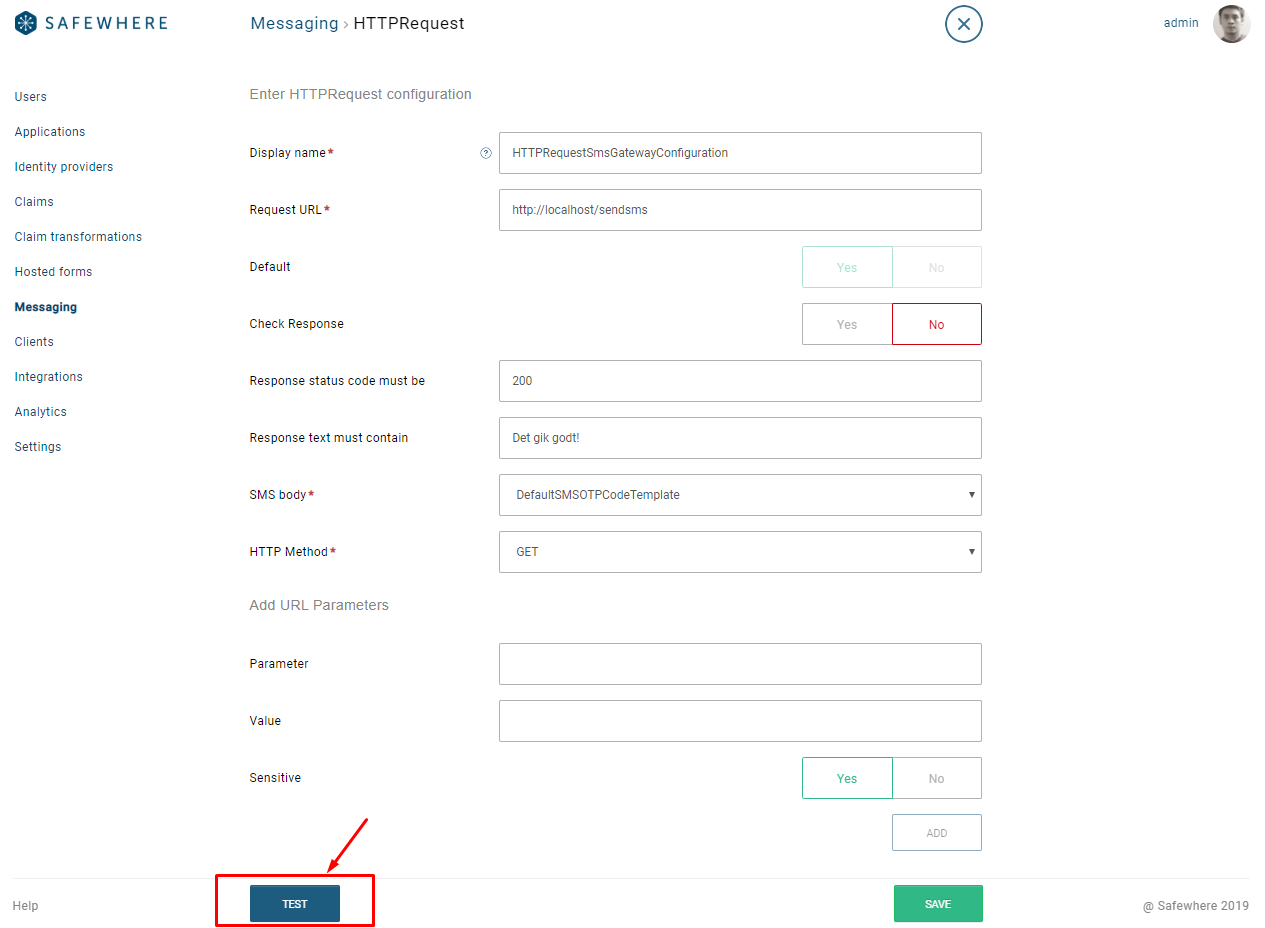
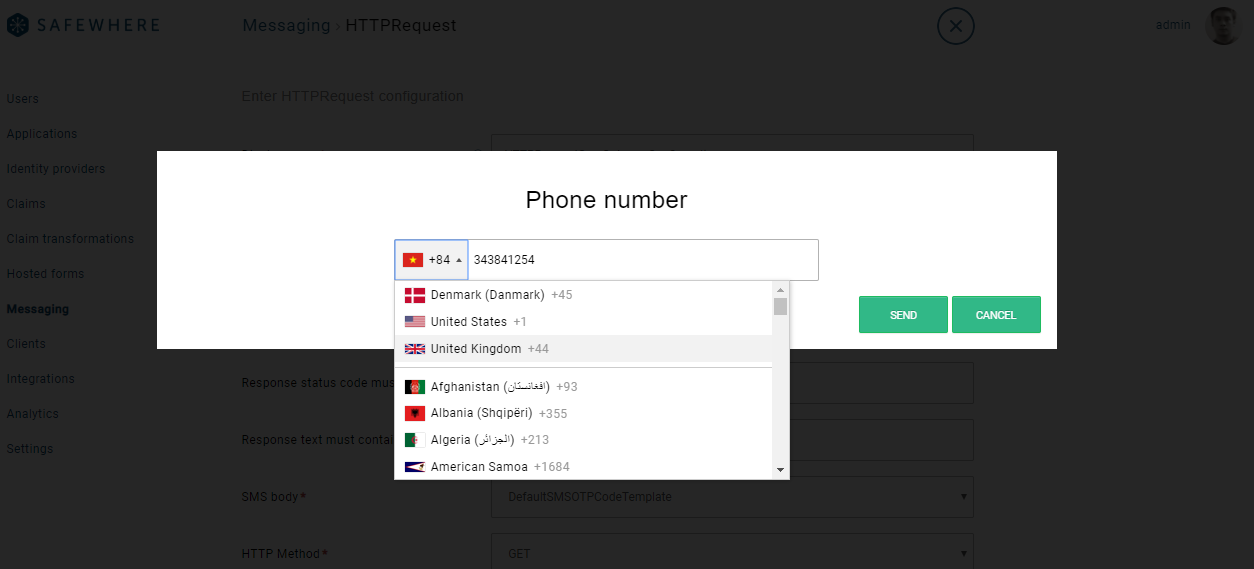
Test functionality for SMS
You can now test sending out SMS from Safewhere Admin from the SMS template screen as well as from the SMS Provider screen:
- From SMS template screen

- From SMS Provider screen
Storing text resources in database
Currently, in order to customize text resources, you will need to edit resource files. The problem with touching file system is that you need to deploy the files on all servers as well as re-deploy them after upgrading to a new version. We have solved those two problems buy adding support for storing custom text resources in database. You will be able to override existing text resources with your own as well as defining new text resources. You can find more information about this new feature.
Improve session management for Identify Admin
We implemented two new counter measures for Identify Admin session management. Firstly, Identify Admin now tracks login sessions in database and will delete the sessions from database after users log out. This means that if an attacker somehow has been able to steal your session data stored in browser and try to use it after you have logged out, Identify Admin will reject the session. Secondly, Identify Admin’s authentication cookies are now pinned to users’ browsers’ fingerprint. As a result, if the cookies are reused from another browser that doesn’t match the original browser, Identify Admin will reject the cookies.
Account lockout
Account lockout is a big feature that we do to improve security for Safewhere Identify. In version 5.6, we finally can complete the feature.
Support more operations
We have added support for account lockout for all remaining places where username and password are used:
- OAuth 2.0 Resource owner password flow.
- STS' username and password endpoint.
- The legacy WCF's service.
- Users are informed about how long accounts are locked in the following situations:
- REST API's "/rest/v2/users" PUT to change password.
- REST API's "/rest/v2/users" PUT to update a user.
- WCF's UpdateUserPassword operattion.
- OAuth 2.0 Resource owner password flow.
- STS' username and password endpoint.
- Username & Password plugin: login & change password.
Unlock users
You can now unlock locked out users by using both the old and new Admin interfaces.
Other improvements for Account lockout
The other small but useful improvements are:
- Log events when user accounts are locked.
- Continue to update last attempt after a user is locked out for security and tracking purpose.
- Separate disabled users and locked out users. This is to fix an annoying usability issue we had in previous versions when we disabled users when they are locked out because Identify's data structure was not ready to support locked out properly.
- Allow for customizing max attempts and lockout duration in System Setup.
Blocking access on connection level
In version 5.5, we added Access control policy feature for controlling when second factor should be triggered. In this version, we continue to expand the Access control policy feature by adding the ability to block access to an application (aka protocol connection). Access to an application can be blocked at two phases:
- When an authentication request first comes to Identify from the application. You can define a policy to stop the login process if, for instance, the user comes or doesn’t come from a specific IP address.
- After Identify creates an authentication session for the user, runs claims transformation, and is about to issue a token to the application. You can define a policy to stop the user if, for instance, his or her token doesn’t have a required role.
Claim selector interceptor
We ship a new interceptor that allows users for selecting what user account he or she wants to use when the identity's claim has multiple values.
Upgrade framework and dependencies
As part of our upgrade process, we have upgraded .NET framework as well as dependencies to latest versions. The upgrade can not only bring new tools for us to build new features but also can fix known security issues of previous versions.
- .NET framework is upgraded from 4.7.2 to 4.8.
- .NET core is upgraded from 2.1 to 3.0. You can find links to download the correct .NET versions on our download pages.
- jQuery is upgraded from 3.3.1 to 3.4.1 for Identify Admin, Identify Runtime and Safewhere Admin
- Bootstrap is upgraded from 4.1.3 to 4.3.1 for Identify Runtime. Please note that we cannot upgrade Bootstrap for the Admin interfaces because that will cause too many breaking changes.
Installer checks for missing frameworks
Identify installer can now check if required .NET framework and .NET core version are installed on servers.
Identify REST API
Support filtering and specifying the attributes to retrieve in the same request
We implemented the SCIM 2.0 specification’s Filter Request functionality where you can specify a list of attributes of the resources and Identify will return those attributes only instead of the whole resource objects. The following example returns just the displayname of every user with a displayname that contains "str":
|
1 |
https://identifyBaseUrl/admin/api/rest/v2/users/.filter?filter=displayName%20co%20%22str%22&attributes=displayName |
Safewhere Admin
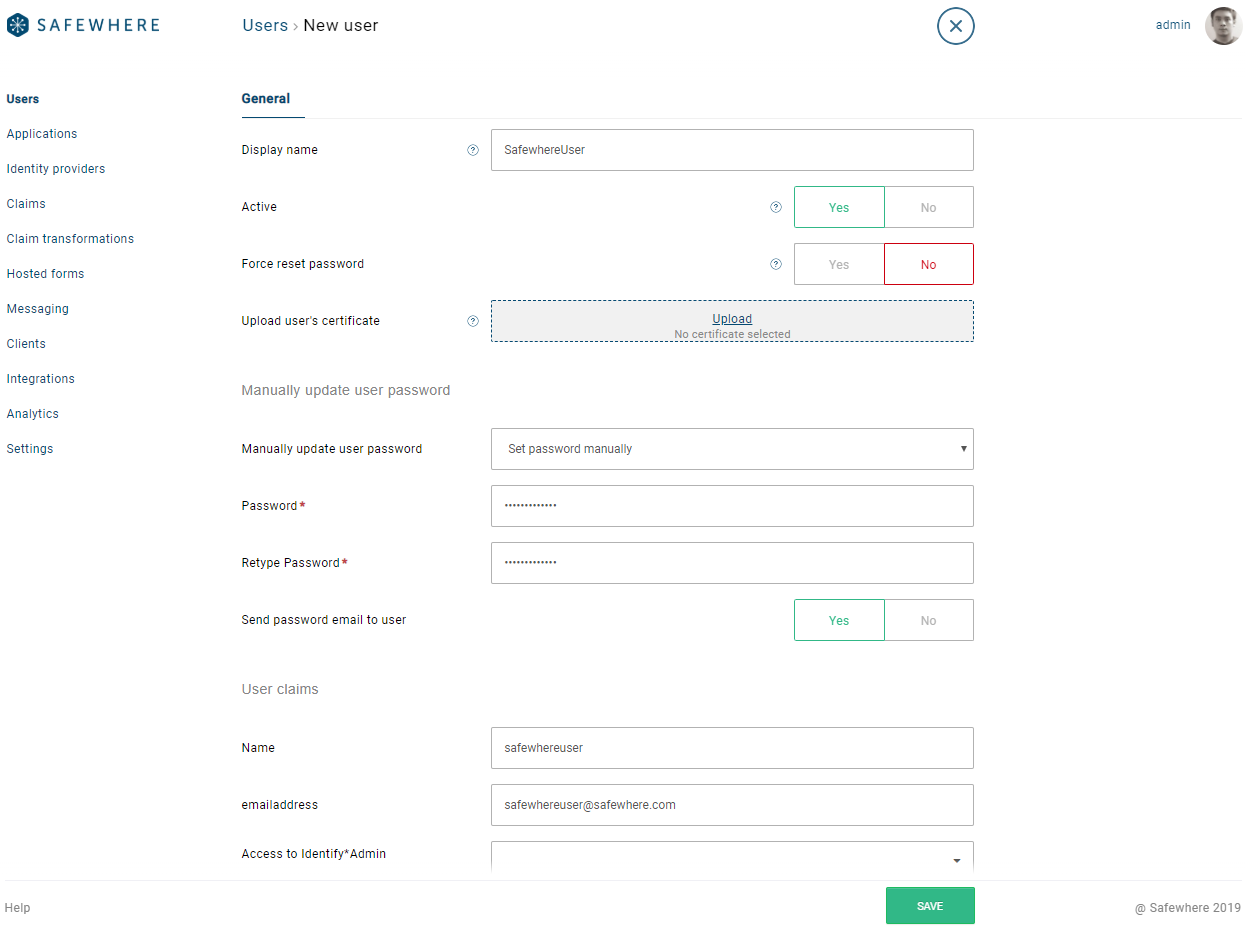
Support sending email or set password when creating new users on Safewhere Admin
We have ported the last important user feature to the new Safewhere Admin: the ability to set passwords as well as to send email out for users to set passwords themselves.
- Manually update user password when creating or editing a user
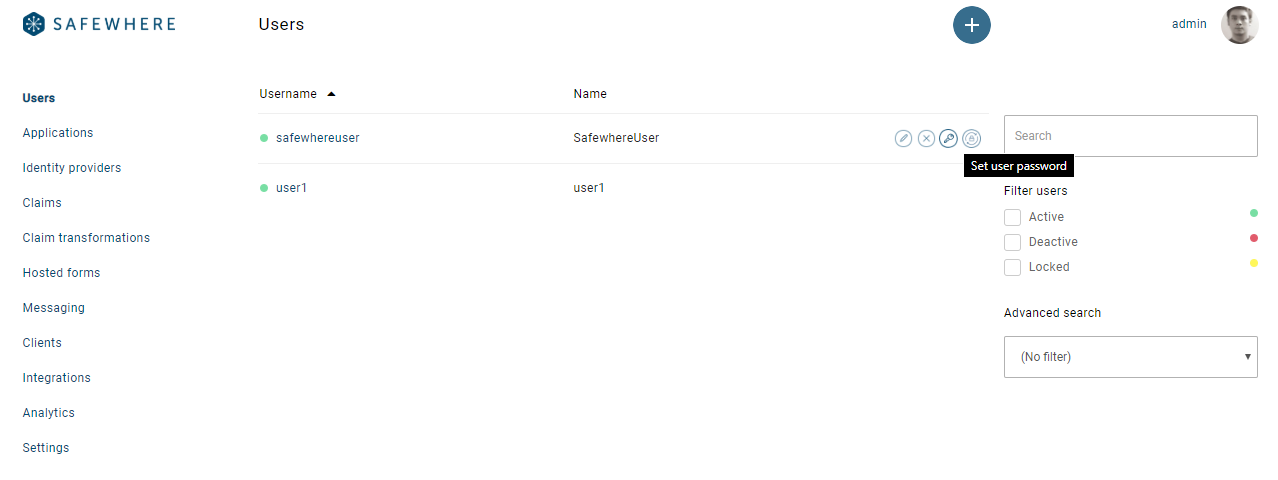
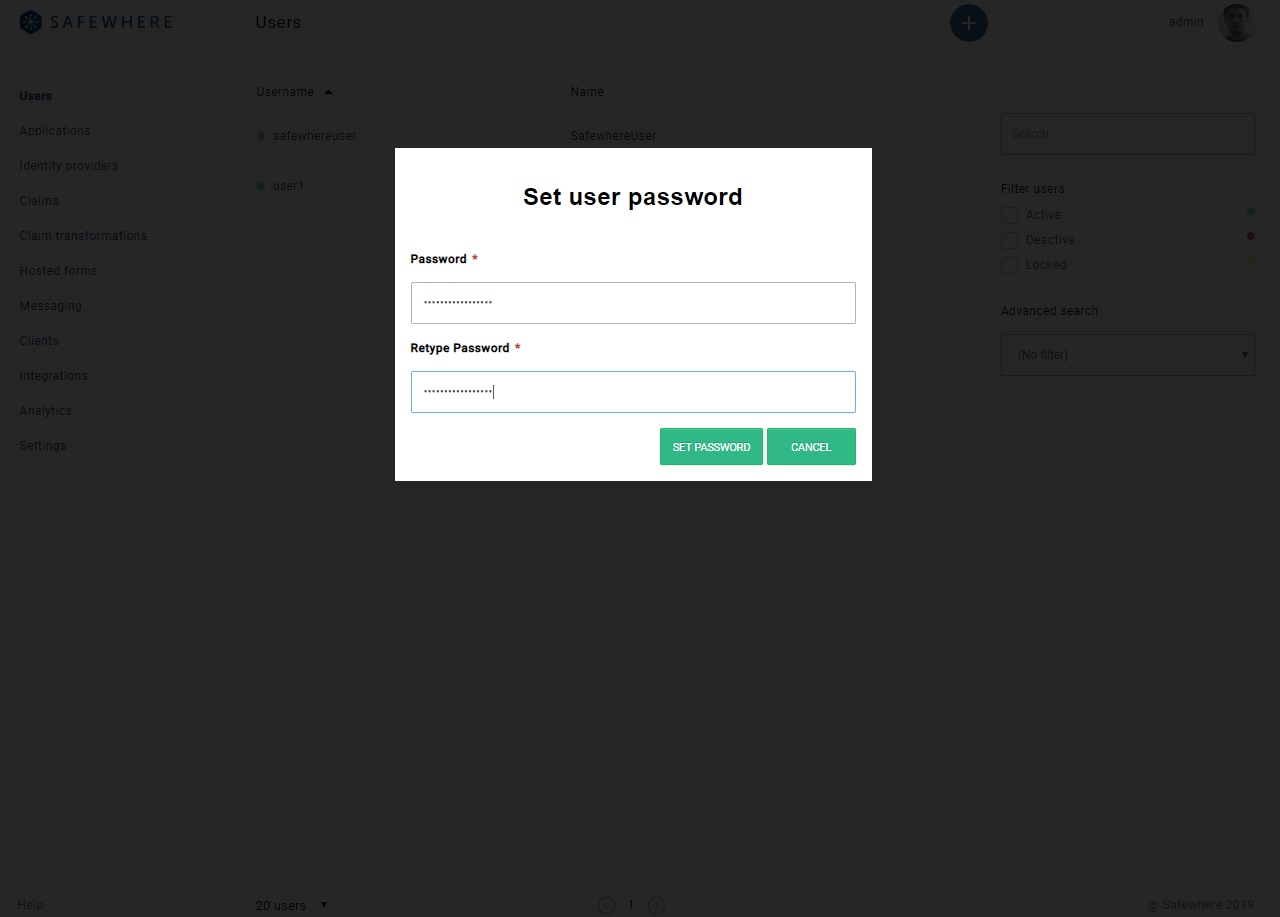
- Manually update user password at user list
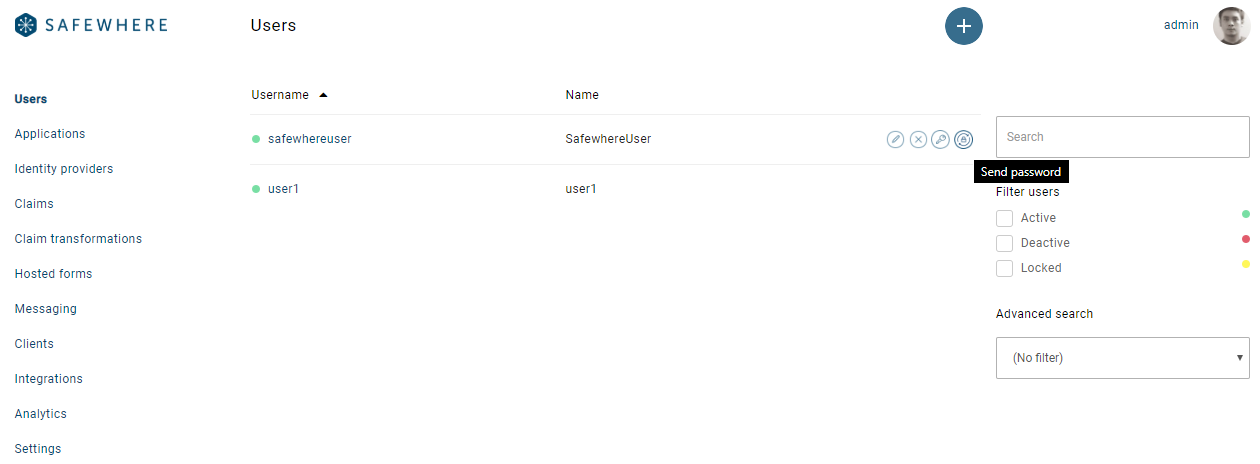
- Send reset password link to a user
Search functionality for System Setup
The System Setup screen has a large amount of settings and sometimes finding a setting that you need can be tedious. The new search feature can help you find the settings you need quickly.
New settings for connectors
We have ported remaining settings to the new Safewhere Admin for the following connectors:
- Google connector
- Twitter connector
- LiveId (Microsoft) connector
- LinkedIn connector
- Facebook connector
- Username & Password
New settings for claim transformations
We have ported remaining settings to the new Safewhere Admin for the following claim transformations:
- Claim Value claim transformation
- Scripting claim transformation
- NameId claim transformation
- Exclude Identify claim transformation
- Exclude pass-through claim transformation
New claim transformations
We have ported remaining transformations to the new Safewhere Admin:
- LDAP claim transformation
- External claim transformation
- SQL Claim Transformation
Other improvements
Some other improvements for Safewhere Admin:
- Show information about "Is Valid", "Is in use" for Certificates list as well as support the search feature.
- You can now use Safewhere Admin and REST API to localize help text and description for Identity Providers and Applications.
- Support for LDAPWS and LDAP Attribute definitions creation
- And a lot of UI bug fixes.
Analysis log type
Analysis log type now can be enabled or disabled from Admin interface.
- Safewhere Admin
 )
)
- Identify Admin

Framework upgrade
Upgraded all 3rd libraries used in both front-end and back-end of Safewhere Admin as well as upgraded its .NET framework to 4.8.
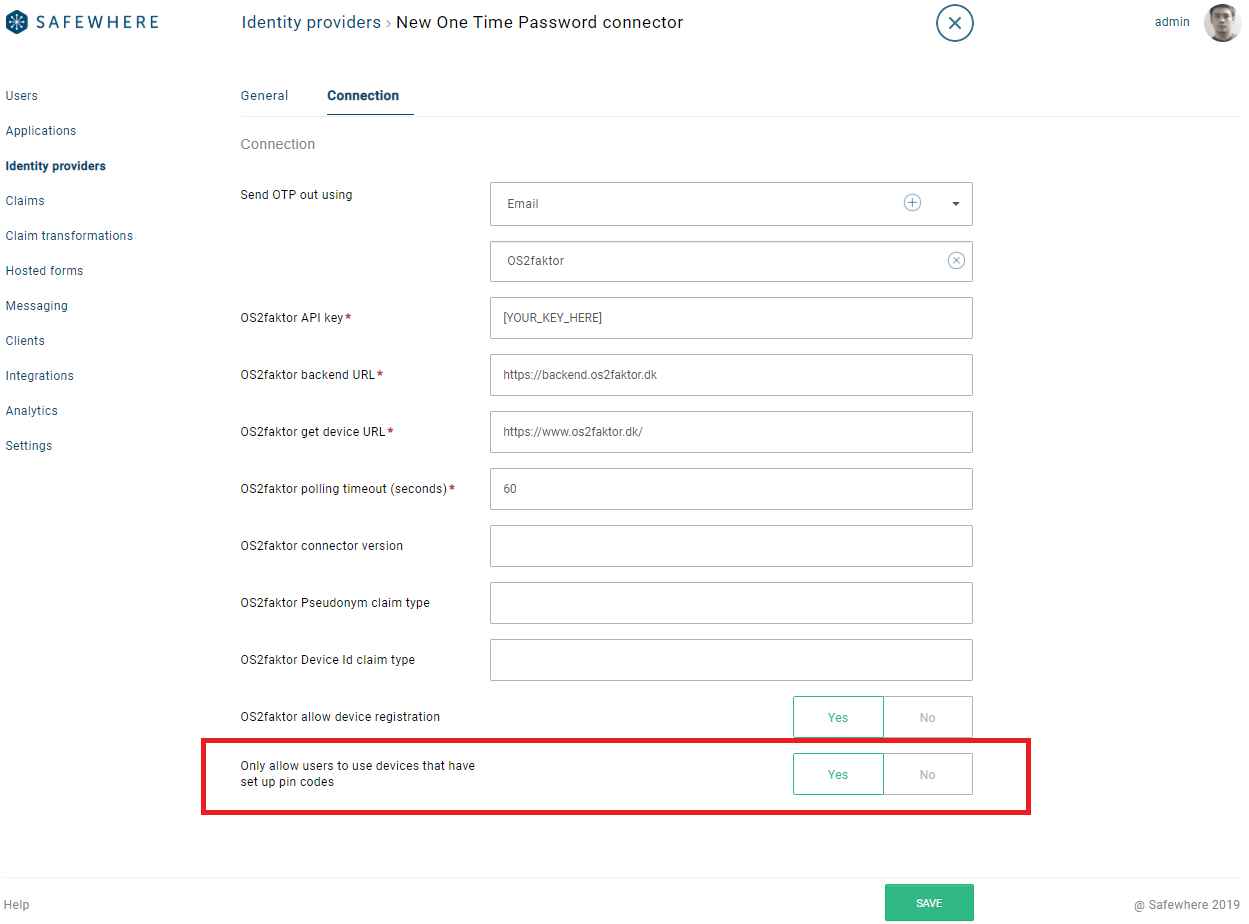
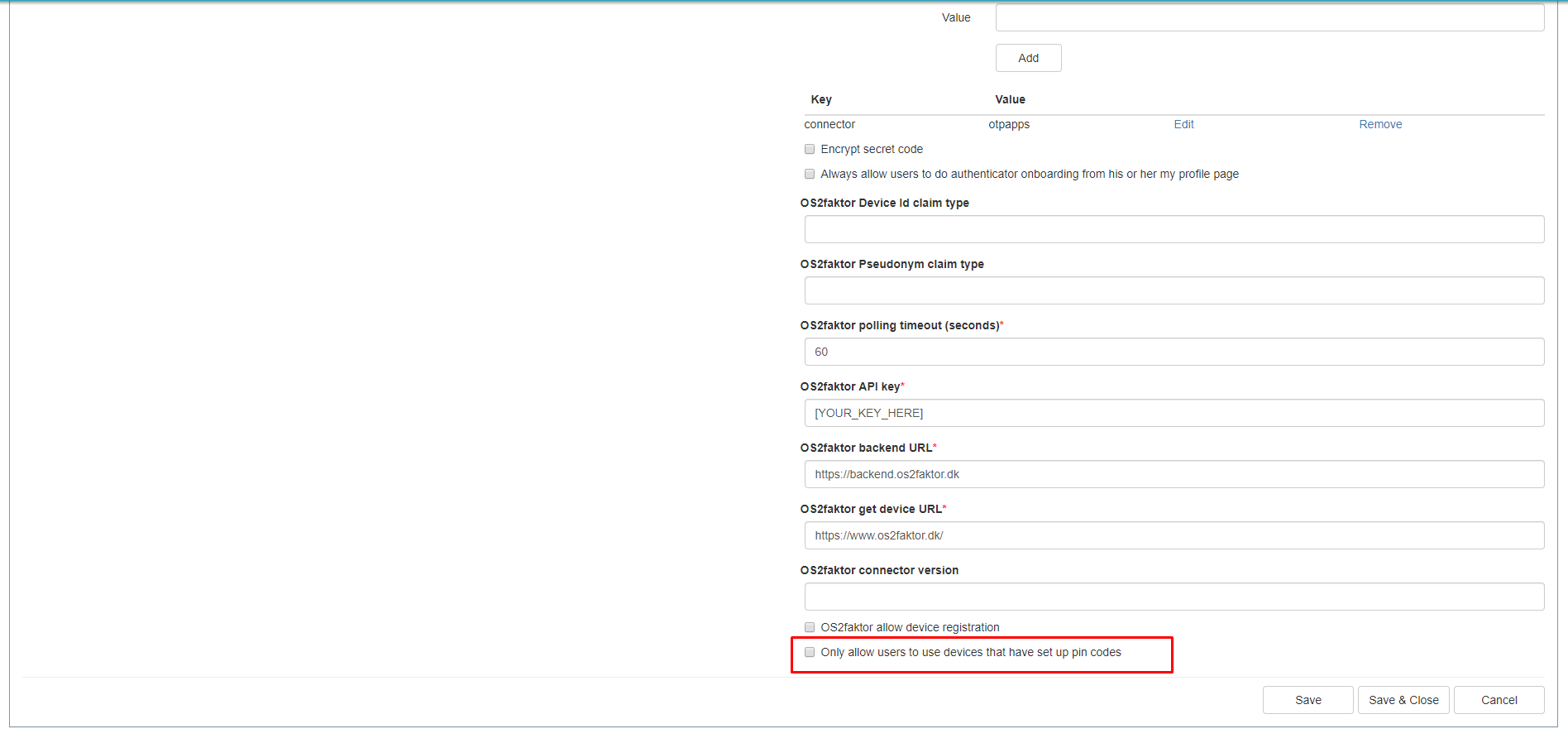
OS2faktor
We added a new setting to control whether to show OS2faktor clients that don’t have pin codes set up:
- Safewhere Admin
- Identify Admin
OAuth 2.0 samples
We updated its samples to demonstrate the new OAuth/OIDC 2.0 features we implemented in this version:
- ASP.NET MVC Sample
- Support PKCE for Authorization Code flow
The Proof Key for Code Exchange (PKCE) feature can be enabled by adding a key named IdentifyOauth2:CodeChallengeMethod into the web.config to specify the method of code challenge.
|
1 |
<add key="IdentifyOauth2:CodeChallengeMethod" value="plain" /> |
Its value can be "S256", "plain" or "none", where "none" mean that the PKCE is disabled. When the PKCE is enabled, the application will generate a random code_verifier and use it when sending authentication request and exchanging the authorization code for an access token.
- Support Request Object
From the 5.6 version, the sample can send a Request Object ("request" parameter) instead of a long list of parameters for Authorization request.
The sample application introduced 2 configuration keys to turn On/Off the Request Object and to specify if the Request Object is signed or not.
|
1 2 |
<add key="IdentifyOauth2:UsingRequestObject" value="true" /> <add key="IdentifyOauth2:SignRequestObject" value="true" /> |
When signing is enabled, the configured "IdentifyOauth2:ClientCertificate" certificate will be used.
- Support ID token hint
For demonstration purpose, the client application only supports Id token hint by a pre-configured value in the web.config:
|
1 |
<add key="IdentifyOauth2:IdTokenHint" value="[token hint here]" /> |
When the key "IdentifyOauth2:IdTokenHint" is present, its value will be used for the id_token_hint parameter in authorization request.
- Support Authentication Type "private_key_jwt"
The Identify OAuth 2 server can authenticates its clients with the private_key_jwt authentication type from 5.6, we updated the ASP.NET MVC sample to support the private_key_jwt.
A couple of keys were added into the web.config:
|
1 2 |
<add key="IdentifyOauth2:AuthenticationType" value="private_key_jwt" /> <add key="IdentifyOauth2:ClientCertificate" value="3C1FD735A4035E3B78D33444DE5327C393AA282E" /> |
To enable the private_key_jwt method, you need to set the "IdentifyOauth2:AuthenticationType" setting to "private_key_jwt" and use a signing certificate's public key to generate a correct client_assertion - a JWT that contains information for client authentication.
- ASP.NET Core Sample
- Support Session Management
OIDC Session Management had been implemented from 5.6 version, the ASP.NET Core sample is chosen to demonstrate the feature.
To enable the session management for the application, add these settings to appsettings.json file:
|
1 2 |
"EnableSessionManagement": "true", "CheckSessionIframeUri": "https://example.safewhere.local/runtime/openidconnect/sessionlogout.idp" |
As a result, the application will add an iframe with the src attribute set to the CheckSessionIframeUri setting so that it can communicate with Identify as an Authorization Server for session state changes in the background.
- Support POST Logout
You can enable this feature by adding a key to appsettings.json file:
|
1 |
"EnablePostLogout": "true" |
By enabling it, the sample application will render a form for "/runtime/openidconnect/logout.idp" post action.
The POST logout endpoint requires id_token_hint and post_logout_redirect_uri so the SP application should prepare these data for the form post.
Bug fixes
Fixed: #66391 Identify Audit - Issued claims are not logged
Fixed: #64817 Emails aren’t sent to users when when input emails contain spaces
Fixed: #65441 WSFED - logout is failed when there are two protocol connections whose one reply url (e.g. https://safewhere.com/app1) is a sub string of the other reply url (e.g. https://safewhere.com/app11)
Fixed: #27218 When replicating tenant to new server, the signing certificate isn't preselected, but SSL certificate is
Fixed: #64828 Username in email subject is wrong when username and email mismatch in Reset Password form
Fixed: #65236 Home Realm Discovery rules are lost when editing a protocol with System Setup’s Show Home Realm Discovery setting is false
Fixed: #65884 SAMLResponse is responded to wrong audience when a connection has multiple Entity Identifiers.
Fixed: #65434 OS2faktor - Unable to authenticate with devices associated with CPR
Fixed: #62950 [Runtime] JS error throws when trying to access to the /idpinitiated endpoint if the connection “Identify runtime connection” is unavailable
Fixed: #63701 [REST API] Create user API must check if the number of users does not exceed the MaxNumberOfAllowedUniqueUsers license setting.
Fixed: #63996 [SWAdmin OTP] Hide OTP delivery interval when only Authenticator method is used
Fixed: #64040 [SWAdmin][SAML2 Application][SAML2 Identity provider] Hyperlink should be blue color
Fixed: #64839 [Hosted form] Upper first letter for form 'Renew Password email sent success'
Fixed: #64847 [SWAdmin][SAML Identity Provider] Change text of "Default requested authentication context class" to "Authentication context method class"
Fixed: #64851 [SWAdmin][SAML2][WSFED] Change text "Enable for mobile users" to "Enable for mobile use"
Fixed: #64853 [SWAdmin] missing the text for the key: Client_Implementation_Framework at the existed client
Fixed: #64861 [SWAdmin][System][Security] Text of Security token resolver factory is not displayed fully
Fixed: #65017 [SWadmin] Add value claim transformation - The selected value is not added when adding the value for the multi discrete claim
Fixed: #65320 [SWAdmin][Settings][IE] Navigation arrows are not displayed
Fixed: #65403 [SWAdmin][Claims] Change text of "Filter users" to "Filter claims"
Fixed: #65409 [SWAdmin][Users][Advanced search] Cannot load selected value of multi discrete claim
Fixed: #65668 [SWAdmin] Cannot update value for "Extra HRD rules that are run after the above rules and other static rules "
Fixed: #65868 [SWadmin] The LoA text at Authentication context method class mapping has broken the UI
Fixed: #65972 [SWAdmin] The username is empty at the IEventConsumer
Hosted form
Fixed: The UserNamePasswordAuthentication view always showed “Please notice that both {{ Model.NameClaim }} and password are case sensitive” even if you configure the connection to use case insensitive. The bug is now fixed. If you have already used the view on hosted form, you will need to update the hosted form view manually buy using either REST API for Safewhere Admin UI.
Identify configurator
Fixed: Due to a nasty bug, Identify process used to have write access to its own web folders. The bug has now been fixed.
Breaking changes
When upgrading Identify instance from previous version, you may experience some following unexpected issues or changes:
- When updating the OAuth2.0 protocol connection, you need to specify the token endpoint authentication method info that your Service provider uses. Here is the known authentication method that Identify uses for its Service providers:
- SafewhereAdmin connection: it uses ClientSecretPost
- Identify OAuth2 Token for REST APIs connection: it uses ClientSecretBasic
